Experimental Post-quantum cryptography support
With the approaching standardization for post-quantum cryptography (PQC), Venafi is adding experimental support for post-quantum cryptographic algorithms in CodeSign Protect. This will allow you to start experimenting with these algorithms.
Experimental post-quantum signing key algorithms are supported in CodeSign Protect clients for signing and verification, though it must be enabled on the Trust Protection Platform server before it can be used. Following the steps in this guide, you will be able to list, sign, and verify using experimental PQC signing algorithms (subject to the limitations outlined below).
WARNING! This feature it is experimental and is intended to help you start planning for future PQC migration.
About this article
The purpose of this article is to get you started experimenting with using PQC algorithms in CodeSign Protect. This article assumes that you have familiarity with CodeSign Protect, so not all the steps are documented in-depth. Where applicable, we've included links to the product documentation where less experienced users can get the information they need to complete the steps.
Supported algorithms
Experimental post-quantum signing key algorithms supported:
-
ML-DSA - Module-Lattice-Based Digital Signature Standard (CRYSTALS-Dilithium)
-
SLH-DSA - Stateless Hash-Based Digital Signature Standard (SPHINCS+)
-
Falcon (for TLS certificates only)
Limitations and considerations
-
PQC must be enabled on all Trust Protection Platform servers in the cluster
-
PQC signing key algorithms are supported for CodeSign Protect Certificate and Key Pair single and per-user environments
-
PQC environments must use "Software" as the key storage location
-
All PQC-related features in Venafi Configuration Console, the web console, and CodeSign Protect clients will have an “Experimental” label
-
Processing time for using PQC signing algorithms will be higher due to the increased key sizes
-
Experimental PQC signing algorithms are only supported for code signing and verification with the CodeSign Protect clients, libhsm API, and non-Venafi applications using PKCS#11 (if those applications support it)
-
PQC support is enabled by default on all CodeSign Protect clients. You can optionally disable it with this CLI command:
*config option -name "Enable PQ Experimental" -value 0
Replace
*configwith the specific client -
Experimental PQC signing algorithms for TLS server certificates are only supported with the built-in self-signed CA
-
Certificates using PQC signing algorithms can only be downloaded in a limited set of formats (DER, PEM (PKCS #8), and PKCS #7) and there is no guarantee of interoperability
-
Code Signing operations are tracked as statistics (shown in the CodeSign Protect dashboard), but are not tracked in the Signing Archive. Only signing operations using non-PQC signing algorithms will be tracked in the Signing Archive
Setting up PQC in CodeSign Protect
This section walks you through each step needed to enable experimental PQC support.
NOTE The steps below don't exhaustively document each step. They only highlight the actions that are needed to activate PQC. Links to more complete documentation are provided where relevant.
Step 1: Activate PQC on the Trust Protection Platform server
PQC is not enabled by default when you install Trust Protection Platform 24.1. To activate this capability, please get in touch with Venafi and we will provide you the activation instructions.
Activating PQC on the Trust Protection Platform server affects the following:
-
Availability of PQC algorithms for use with CodeSign Protect Environment templates (VCC)
-
Availability of PQC algorithms for use with CodeSign Protect Environments (Aperture)
-
Availability of CodeSign Protect environments using PQC algorithms to CodeSigning clients (LibHSM & REST API)
-
Availability of PQC algorithms for use creating certificates in TLS Protect (WebAdmin or Aperture)
Step 2: Set up a self-signed CA template
If you don’t have a self-signed CA template set up already, you’ll need to set one up. If you already have one, you can skip to the next step. If you're unsure, follow the link below.
Make sure that your self-signed CA template has Digital Signature and Code Signing checked on the Key Usage tab.
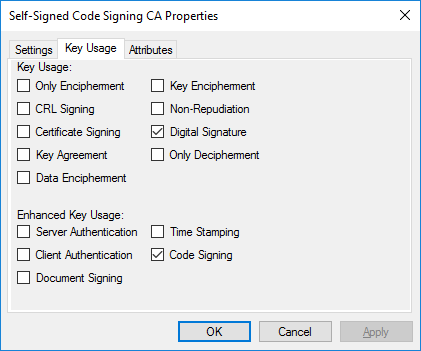
For instructions, see Create a self-signed CA template.
Step 3: Create a Key Pair environment template for PQC
The environment template is where you'll specify which experimental PQC algorithms you want to make available.
Set up a new Key Pair environment template. From the Keys tab, select which PQC algorithms you want to make available when Project Owners use this template.
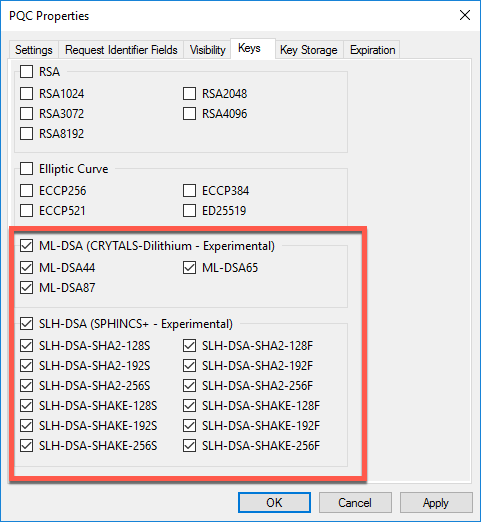
Complete the remaining tabs according to the documentation.
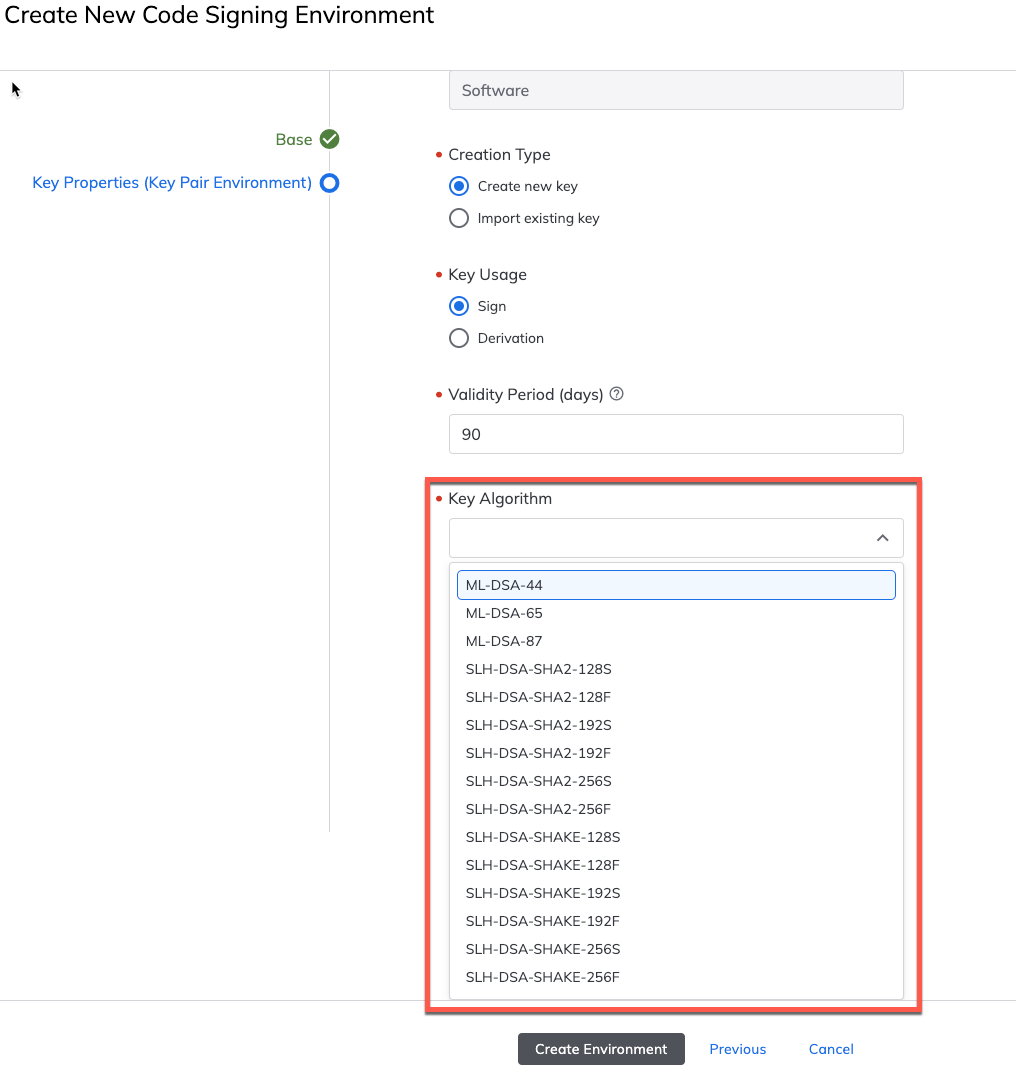
Step 4: Create a Key Pair environment using the PQC environment template
You can either add a new environment to an existing project or create a new project and add the environment to that.
When creating the environment, be sure to select Key Pair as the Environment Type, and then select the PQC environment template (from the previous step) as the Environment Template.
With these selected, you'll then see the allowed PQC algorithms from the Key Algorithm drop down selector.
Step 5: Sign with the PQ keys
Experimental PQC signing algorithms are only supported for code signing and verification with the CodeSign Protect clients, libhsm API, and non-Venafi applications using PKCS#11 (if those applications support it).
Obtain grant
If the key user doesn't already have a grant, one will need to be requested.
pkcs11config getgrant --host <tpp-hostname>
You will be prompted for the key user's credentials. The user must be specified as a key user on the project.
Sync keystore with backend
Sync your local keystore with CodeSign Protect.
pkcs11config sync
List keys
List the keys that are available to the key user.
pkcs11config listobjects
You'll need the Label value of the key that you want to sign with in the next step.
Sign using pkcs11config
In this example, the file sign_me is signed using a PQC key identified by the label PQ-test-MLDSA. The signature is stored in the sign_me.sig file.
pkcs11config sign --label PQ-test-MLDSA --file sign_me --output sign_me.sig
Verify the signature
You can now verify the signature.
pkcs11config verify --label PQ-test-MLDSA --file sign_me --in sign_me.sig
TLS certificate support
While the focus of this document is CodeSign Protect, experimental post-quantum (PQ) signing key algorithms are supported for TLS Server Certificates
-
WebAdmin Policy tree: Add > Server Certificate
-
Aperture: Certificate inventory > Create a New Certificate
NOTE In the Certificate Inventory page in Aperture, the Key Size column (in default view) will appear as 0 for PQC signatures because PQC signatures use a parameter set instead of key size.