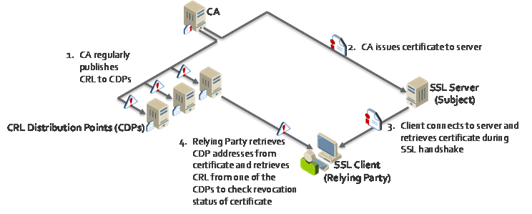
Understanding CRLs and CDPs
Before discussing CRLs and CDPs, it is helpful to distinguish two roles: the Subject and the Relying Party.
A Subject is a person or system to which a certificate is issued. A Relying Party is the person and/or system that uses a Subject’s certificate for secure communications or verifying digital signatures. For example, a web server to which an SSL certificate is issued is a Subject and the Relying Party is an user connecting to the web server with a browser.
A certificate authority (CA) revokes a certificate when it is no longer trustworthy, such as when a Subject is misidentified in a certificate or the Subject’s private key is compromised. CAs publish certificate revocation lists (CRLs) so Relying Parties know which certificates have been revoked.
Revocation Checking Process: Publishing CRLs, issuance of certificates, and checking the revocation status of a certificate
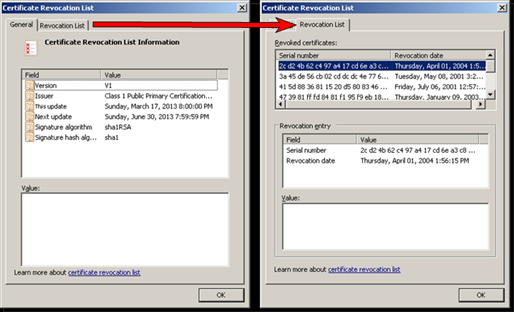
CRLs include a list of certificates a CA has revoked as well as other information. CRLs should include two dates: the date on which the CRL was last updated (Published Date) and the date on which the CRL will be updated next (NextUpdate). The period of time between these two dates is the validity period of the CRL. CAs should update the CRL on all CDPs on or before the date specified in the NextUpdate field of a CRL. If a Relying Party retrieves a CRL with a NextUpdate date that has passed, the Relying Party should not continue. This can result in downtime if the Relying Party is an automated system. Therefore, it is critical that CRLs be kept up-to-date. The following image shows a sample CRL.
Sample CRL
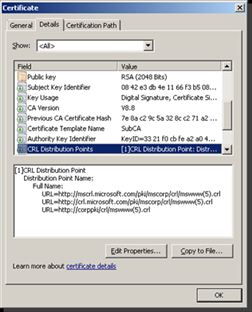
CAs publish CRLs in one or more locations, called CRL Distribution Points (CDPs), where they can be easily accessed by Relying Parties. The CA places the address(es) of CDP(s) for its CRL in each certificate it issues so that Relying Parties know their locations. The following figure shows a sample certificate that contains three CDP locations in the CDP extension.
CDP Extension in a Certificate
Certificate Distribution Point Monitoring in Trust Protection Foundation
CRLs are digitally signed by the CA, which is how you validate their authenticity, since you use an insecure connection to retrieve them (for example, HTTP; you should not use HTTPS). If a CDP goes down, it can result in a multi-system outage for all certificates that check revocation status (including the CyberArk Agent). The CDP checking functionality in Trust Protection Foundation scales well for systems of all sizes, such that frequent checks (including hourly checks) don't have a negative impact on system performance.
The CDP checking functionality also updates the revocation status of any affected certificates each time the CRL is loaded.
Trust Protection Foundation's custom endpoints functionality allows you to use a load balancer for high availability monitoring, while still allowing Trust Protection Foundation to connect to every endpoint covered by the load balancer to ensure all your systems are working properly.