Validating Certificate Revocation Lists - Overview
Ensuring your certificate validation statuses match the status of the certificate on the CA is important. If a CRL expires or is unavailable, it can cause multiple system outages for all systems with certificates that rely on that CRL Distribution Point (CDP) for verification. Trust Protection Foundation checks the CDPs on a scheduled basis to verify that the endpoint is active. If a CDP goes down, you need to take immediate action to prevent outages. The Trust Protection Foundation Certificate Revocation List (CRL) Verification Service verifies CRLs to ensure that they are valid and available for revocation checking. If a CRL is within a configurable time-period prior to expiration, the service sends a notification to one or more administrators so that they can ensure it is updated.
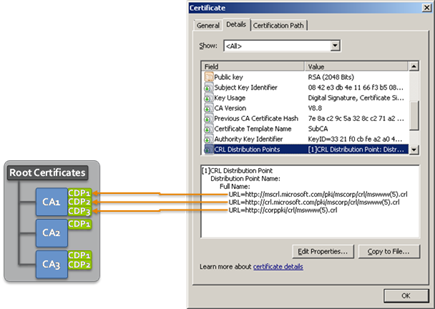
The CRL Verification Service checks CRLs on each CDP on which they are located. To accomplish this, the CDP location information for each verified CRL is configured in Trust Protection Foundation on CA certificates in the Policy Tree Roots tree. CDP information is added to Trust Protection Foundation in three ways:
- Automatic population: Trust Protection Foundation scans certificates in the inventory, and searches for information about the certificate's issuer. If the CDP for a certificate is not already in the Policy Tree Roots tree, it is added. For more information see CDP Information from Certificates Used to Add CDP Entries Automatically.
-
New CA Certificate: When a CA certificate is added to the Roots tree, Trust Protection Foundation checks the certificates in the Policy tree that have been issued by that CA and adds any discovered CDPs to the CA certificate object.
- Manually: CDP entries can be added to an individual CA certificate object by entering the CDP location information (the URL to the CDP).
- Revocation checking: Trust Protection Foundation checks for revoked certificates on a scheduled basis, automatically. To learn more about how revocation checking works, see Checking the revocation status of certificates.
CDP Information from Certificates Used to Add CDP Entries Automatically
The time-frame prior to the NextUpdate date when the CRL Verification Service will send notification warning of expiration is configurable using the Expiry Notification Percentage. The Expiry Notification Percentage is a percentage of the CRL validity period (Published Date to NextUpdate) and is used to determine how long before CRL expiration that the CRL Verification Service should send expiration warning notifications.
NOTE The Next Update attribute is functionally the expiration date of the CRL. Thus, you can extrapolate the validity period of the CRL by subtracting the Published Date from the Next Update.
Expiry Notification Percentage

This percentage is set at the root of the Roots tree (to apply to all CA certificates) or on individual CA certificates (overriding the value set at the root). Each time that the CRL Verification service runs, it connects to each CDP, retrieves the CRL, and calculates the amount of time until the NextUpdate date. If that time is less than the Expiry Notification Percentage, a notification is sent.
About Supported URL Formats
Trust Protection Foundation CRL Verification service supports the following URL formats for CDPs:
- HTTP (e.g.
HTTP://crl.venafi.com/enterprise.crl) - FILE (e.g.
FILE://crl.venafi.com/CertEnroll/QA-CA.crl); format requiresFILE:followed by any valid Windows path.
Trust Protection Foundation expects all endpoints to be configured for anonymous authentication. When Trust Protection Foundation is installed on a Windows server that is joined to a domain, Trust Protection Foundation leverages the permissions of the account that VPlatform is running under if a FILE endpoint requires authentication.