Guidelines for agent CRL Checking
The agent connects to the Trust Protection Foundation server using HTTPS and checks the revocation status of the Venafi Operational Certificate on the Trust Protection Foundation server by retrieving a certificate revocation list (CRL). To ensure that this process works correctly, review the following guidelines:
- All certificates—those used on the Trust Protection Foundation server hosting the client subsystem, and CA certificates that are found in the chain—must include a valid CRL distribution point (CDP) extension with at least one CDP address that is accessible by the agents.
- HTTP-based CDPs are supported.
- LDAP, FTP, and file-based CDPs are not supported by the agent. Make sure that your CDPs are accessible through the HTTP protocol (non-SSL).
- Delta CRLs are supported but not required.
NOTE If a delta CRL is specified within the base CRL, make sure that it is accessible and valid.
The following diagram shows how agent CRL checking works from the time that the root CA posts a CRL to when Trust Protection Foundation and the agent checks revocation lists.
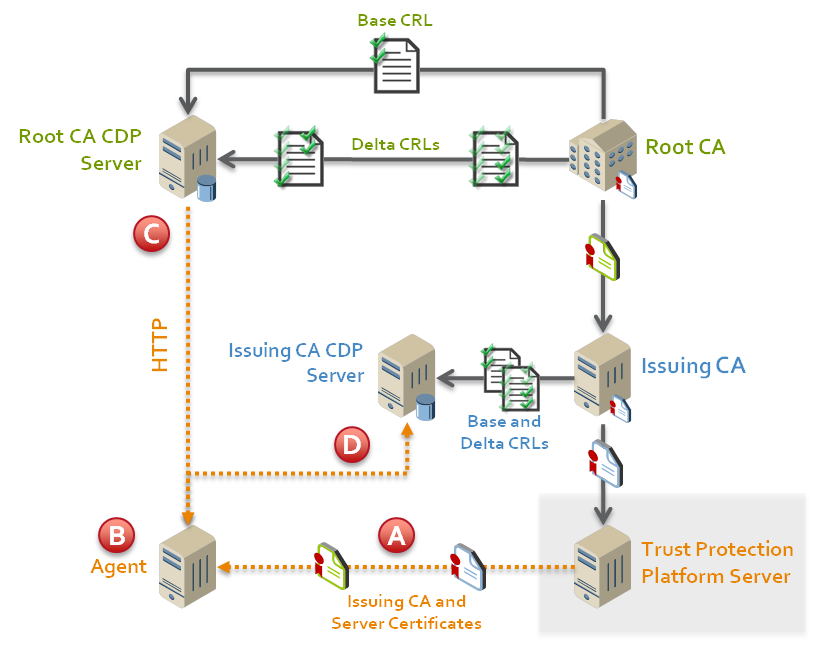
- Trust Protection Foundation server sends Issuing CA and server certificates to the agent.
- The Agent validates each certificate's signature using the root certificate stored in curl-ca-bundle.crt.
- The Agent checks the revocation status of the Issuing CA certificate.
- The Agent checks the revocation status of the Trust Protection Foundation server certificate.