Integrating with Microsoft Intune
Microsoft Intune is a cloud-based enterprise mobility management (EMM) service that enables your workforce to be productive while keeping your corporate data protected. It is available in the Azure portal, and it offers the following benefits:
- Manages the devices your workforce uses to access company data
- Manages the mobile apps your workforce uses
- Protects your company information by helping to control the way your workforce accesses and shares it
- Ensures devices and apps comply with company security requirements
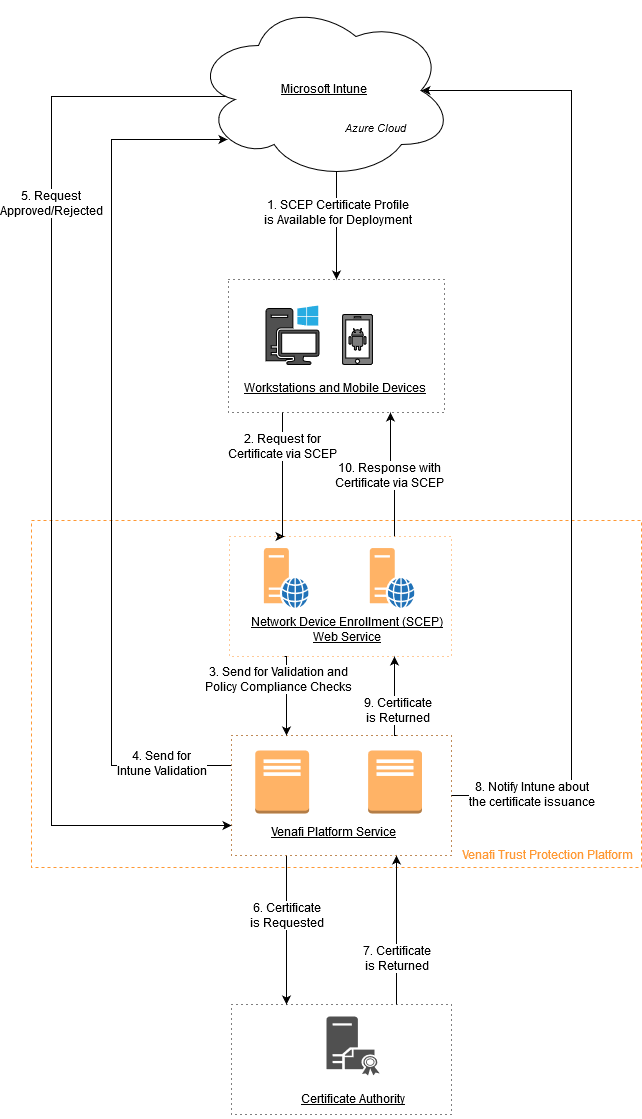
- The Microsoft Intune administrator creates an SCEP certificate profile in Microsoft Intune. Microsoft Intune deploys the profile to the specified group of devices.
- The device requests a certificate from the Network Device Enrollment (SCEP) Web Service via the SCEP protocol.
- The certificate request is sent for validation and policy compliance checks.
- Venafi Platform Service validates the request with Microsoft Intune.
- Microsoft Intune approves or rejects the certificate request.
- In case of approval, Venafi Platform Service requests a certificate from the configured Certificate Authority.
- The Certificate Authority issues the certificate and returns it to Venafi Platform Service.
- Microsoft Intune is notified for the certificate issuance. In case of success, details about the issued certificate are sent. In case of failure, the reason for the failure is sent.
- Venafi Platform Service returns the certificate to Network Device Enrollment (SCEP) Web Service.
- Network Device Enrollment (SCEP) Web Service returns the certificate to the device via SCEP protocol.
This topic provides the steps necessary to integrate Microsoft Intune with Trust Protection Platform. This procedure includes the following steps:
NOTE Before beginning these steps, make sure that all servers of the Venafi Platform Service can make outbound HTTPS connections to Microsoft Azure Cloud.
This procedure describes how to register Trust Protection Platform with Microsoft Intune. There are three pieces of data produced during this procedure that you will need in order to complete the subsequent steps in this procedure:
- Application (client) ID
-
Credentials used to prove the application’s identity
- Certificates
- Client secret
- Tenant Name
The steps below prompt you to save these items as you generate them.
- Sign in to the Azure Portal.
- Click Azure Active Directory.
- Click App registrations.
- Click New registration.
- Enter a name for this registration in the Name field. Leave the other fields as-is.
- Click Register.
- Copy the Application (client) ID value and store it.
-
Click Certificates & Secrets.
Create a new secret using one of the following methods:
-
(Recommended). Click Certificates > Upload Certificate. Select a certificate, and then click Add.
NOTE You'll need to either upload or link this certificate in Trust Protection Platform in a subsequent step.
-
Click Client Secrets > New client secret. In the Description box, enter any string. Select an expiration period.
NOTE After the expiration period, the client secret will need to be re-created. It is recommended that you use the same validity period between Intune and Trust Protection Platform, which will be configured in a subsequent step.
Click Add.
This creates an application password. Copy the application password and store it along with the Application (client) ID copied in a previous step. You must copy the application password before leaving this page. If you leave the page prior to copying the password, you need to create a new application password by repeating this step.
-
- On the API Permissions page, click API Permissions > Add a permission.
- Click Intune.
- Click Application permissions.
- Select scep_challenge_provider and then click on Add permissions.
- Click Add a permission again.
-
Click Microsoft Graph > Application permissions, and then select
Application.Read.All.NOTE If upgrading from TPP 22.2 or earlier, see Upgrading TPP and Intune migration from ADAL to MSAL .
-
Click Add Permissions.
- On the API Permissions page, click Grant admin consent for <account name>, and then click Yes.
-
Click Azure Active Directory. Copy the Primary domain value, which is usually in the format <value>.onmicrosoft.com.
NOTE The following steps walk through a typical scenario of setting up RA signing and encryption credentials. The policy structure and file names used are examples. Customize your folder and file names as necessary.
If you already have RA signing and/or encryption certificate credentials for Network Device Enrollment, you can skip this step and proceed to Step 3: Create a CA Template to issue certificates for endpoints. If not, follow the steps below:
-
In the Trust Protection PlatformPolicy Tree console, open the Policy Tree and create policies to store the RA certificates and templates. This example uses the following policies:
- Policy > Administration > CA Templates > Intune > RA
- Policy > Administration > Credentials > Intune
- Policy > Certificates > Intune > RA
NOTE For steps on creating new objects in Policy Tree, see Adding objects to the policy tree.
-
Prepare CA templates for RA certificates.
IMPORTANT Steps a-c below apply to Active Directory Certificate Service. If you are using another service, prepare certificate templates that have the following properties:
 See properties
See properties
For the encryption certificate:
- Key Usage: Key Encipherment
- Enhanced Key Usage: Certificate Request Agent (1.3.6.1.4.1.311.20.2.1)
For the signing certificate:
- Key usage: Digital Signature
- Enhanced key usage: Certificate Request Agent (1.3.6.1.4.1.311.20.2.1)
NOTE In the following steps, we suggest cloning the templates on your AD CS and to set Subject Name to Supplied in the request.
To prepare the RA encryption and signing templates, follow these steps:
- Create a new Username Credential under the Policy > Administration > Credentials policy. Use the credentials of the AD account that that is allowed to request certificates from AD CS.
-
For the encryption template, create a new CA Template (usually a Microsoft CA template) under the Policy > Administration > CA Templates > Intune > RA policy.
- In the CA Name field, enter a name for this CA template. This example uses SCEP RA Encryption Only Template as the name.
- Complete the CA Name, Hostname, and Service Name fields, and select the credential created in the previous step.
- Next to the Template box, click Retrieve, and then select VenafiCEPEncryption as template.
- Check the Subject Alt Name Enabled checkbox.
- Click Save.
-
For the signing template, create a new CA Template (usually a Microsoft CA template) under the Policy > Administration > CA Templates > Intune > RA policy.
- In the CA Name field, enter a name for this CA template. This example uses SCEP RA Signing Only Template as the name.
- Complete the CA Name, Hostname, and Service Name fields, and select the same credential that was used for the encryption CA template above.
- Next to the Template box, click Retrieve, and then select VenafiEnrollmentAgent(Offlinerequest) as the template.
- Check Subject Alt Name Enabled checkbox.
- Click Save.
-
Prepare RA certificates for signing and encryption
-
Create a new Device Certificate object under the Policy > Certificates > Intune > RA policy.
- In the Certificate Name field, enter a name for this CA template. This example uses SCEP Encryption Only as the name.
- Set the Common Name to the name of the Trust Protection Platform server.
- In the Subject Alt Name(s) section, click Add / Remove and then set the SAN DNS to the fully qualified domain name (FQDN) of the Trust Protection Platform server.
- In the CA Template field, select the previously-created template named SCEP RA Encryption Only Template.
- Ensure the Management Type is set to Enrollment.
- Click Save.
- Click Renew Now.
-
Create a new Device Certificate object under Policy > Certificates > Intune > RA policy.
- In the Certificate Name field, enter a name for this CA template. This example uses SCEP Signing Only as the name.
- Set the Common Name to the name of the Trust Protection Platform server.
- In the Subject Alt Name(s) section, click Add / Remove and then set the SAN DNS to the fully qualified domain name (FQDN) of the Trust Protection Platform server.
- In the CA Template field, select the previously-created template named SCEP RA Signing Only Template.
- Ensure the Management Type is set to Enrollment.
- Click Save.
- Click Renew Now.
-
-
Prepare RA certificate credentials.
-
Create a new Certificate Credential object under Policy > Administration > Credentials > Intune policy.
- In the Credential Name field, enter a name for this credential. This example uses SCEP Encryption Only Cred as the name.
- In the Certificate Data section, click the Link to existing certificate radio button, and then select your SCEP encryption-only certificate object in the Link to Certificate field. In this example, the certificate object name is SCEP Encryption Only (created in a previous step).
- Click Save.
-
Create a new Certificate Credential object under Policy > Administration > Credentials > Intune policy.
- In the Credential Name field, enter a name for this credential. This example uses SCEP Signing Only Cred as the name.
- In the Certificate Data section, click the Link to existing certificate radio button, and then select your SCEP signing-only certificate object in the Link to Certificate field. In this example, the certificate object name is SCEP Signing Only (created in a previous step).
- Click Save.
-
If you already have CA template for device certificates (make sure that the RA certificate is signed by the CA), you can skip this step and proceed to Step 4: Configure Network Device Enrollment for Microsoft Intune validation. If not, follow the steps below:
NOTE The following steps provide instructions on setting up CA templates with names for specific device types. Customize your CA template names as necessary to match your environment.
- Navigate to Policy > Administration > CA Templates > Intune.
-
Create two CA templates, one named Client Authentication Template and the other named Windows - Client Authentication Template.
Select a template from your certificate authority that has Enhanced Key Usage (EKU) set to Client Authentication and Subject Name set to Supplied in the request.
Make sure all the previous steps are complete.
NOTE The following steps provide instructions on setting up Network Device Enrollment with specific device names. Customize your names as necessary to match your environment.
-
Create the policy structure that matches your use-cases. This example uses the following structure:
- Policy > Administration > Credentials > Intune
- Policy > Certificates > Intune > Client Authentication > Windows
-
Navigate to Policy > Administration > Credentials > Intune and create a new credential object. You'll create either a new Certificate Credential or Password Credential, depending on the type of credential you created in Step 1: Register Trust Protection Platform with Microsoft Intune.
-
If you used a certificate, right click the Intune policy folder and select Add > Credential > Certificate Credential.
Select the corresponding certificate to the one you selected during the application registration step (Intune configuration).
-
If you used a client secret, right click the Intune policy folder and select Add > Credential > Password Credential.
In the password field, specify the Application Secret generated during the application registration step (Intune configuration).
-
-
Go to Platforms > Platforms > your-platform > Network Device Enrollment > Settings.
- In the Certificate Request Authentication section, select Microsoft Intune.
-
Specify Intune Tenant Name, Intune Application ID, and select Intune Application Secret in the Intune Application Credential field.
NOTE When your organization signs up for a Microsoft cloud-based service like Intune, you’re given an initial domain name hosted in Azure Active Directory (AD) that looks like
your-domain.onmicrosoft.com. In this example,your-domainis the name that you need to specify for Intune Tenant Name field. If you use a custom domain name, use that instead. - Click Validate to check the populated settings.
-
In the Default CA, section specify the following:
- Default Certificate Container to Policy > Certificates > Intune > Client Authentication
- Default Certificate Authority to Client Authentication Template.
- RA Signing Certificate Credential to SCEP Signing Only Cred.
- RA Encryption Certificate Credential to SCEP Encryption Only Cred.
- Click Save.
-
Go to Platforms > Platforms > your-platform > Network Device Enrollment > Rules
- Check Support additional CAs configured on policies check box
-
Click Add to add new rule. Specify the following:
In the General section:
- Container to Policy > Certificates > Intune > Client Authentication > Windows
- Certificate Origin to Intune - Client Authentication for Windows
In the Certificate Authority section
- CA Ident to windows (This identifies what kind of certificates are going to be issued)
- Certificate Authority to Windows - Client Authentication Template
- RA Signing Certificate Credential to SCEP Signing Only Cred
- RA Encryption Certificate Credential to SCEP Encryption Only Cred
- Save the popup
Restart IIS on all Trust Protection Platform servers where the Network Device Enrollment component is deployed.
NOTE The steps in this procedure are example steps for a specific configuration. Customize the selections as necessary to support your enviornment.
Create Microsoft IntuneTrusted Certificate device configuration profile
- Obtain the root certificate of the CA that will issue the device certificates. This was defined in Step 3: Create a CA Template to issue certificates for endpoints.
- On the Azure Portal, select Intune and in the Device Configuration section, click Profiles.
- Click Create Profile.
- Provide a Name and Description for the target profile.
- From the Platform dropdown, select the appropriate platform for your environment.
- For Profile Type, select Trusted certificate.
- Click Settings - Configure to select the CA certificate (which was obtained in step 1) to be uploaded for creating the profile.
- Click OK and then Create to create the profile with the settings.
Creating Microsoft Intune SCEP Certificate device configuration profile
- On the Azure Portal, select Intune and in the Device Configuration section, click on Profiles.
- Click on the Create Profile button.
- Provide a Name and Description for the target profile.
- From the Platform dropdown, select the appropriate platform for your environment.
- For Profile Type, select SCEP certificate.
- In the Settings section, provide corresponding certificate attributes as per the certificate profile you would have configured in the Certificate Authority defined in Step 3: Create a CA Template to issue certificates for endpoints.
-
Populate all fields regarding the certificate. Make sure that:
- In the Root Certificate field, you select the Trust Certificate profile created above.
- The Extended key usage is set to at least Client Authentication.
- In the Enrollment Settings section, set the SCEP Server URL to your Network Device Enrollment (SCEP) Web Service. In this example we configured (Step 4: Configure Network Device Enrollment…) Windows as the CA Ident, so the URL usually looks like https://tpp.example.com/vedscep/windows/
- Click OK and then select Create to create the profile.
Once the profiles are created, you would need to assign these to the devices or users.
NOTE Make sure that the SCEP Server URL ends with forward slash /. Otherwise some versions of iOS and macOS may have troubles requesting certificates.
Synchronize the device to trigger the profile installation
- On the Azure Portal, select Intune and then click on Devices. Click on All Device.
- Select the device you would like to synchronize.
- Click Sync. This synchronizes the device with the settings configured.
- Once the synchronization is initiated, the certificate profile settings will be installed to the device. Then the device will request a certificate from the configured SCEP Server URL and the certificate will be installed on the device.