Global Code Signing Configuration tab
In this section, you can set the default storage locations for Certificate Authority Templates, Credentials, and Certificates. To change any of these locations, click the drop-down box and select a new folder.
These locations can be reset in the Environment Templates.
Private Key Generation and Storage
This section lists the available generation and storage locations for code signing private keys. Place a checkmark next to each location you want to use for key storage. The storage locations selected here will be the only locations available in the Environment Templates.
NOTE If you do not have any connected HSMs, then the only option shown is Software, which is the Trust Protection Foundation Secret Store. To select an HSM, you first need to configure an HSM. See Creating a HSM connector for instruction on connecting an HSM.
-
Key Users may not have other roles in the same project. Checking this box restricts users assigned as Key Users or members of a Key User group from having any other role on the code signing project.
NOTE User roles in the project are checked when the key is used, not when the project is created or edited. The reason for this is that group membership is dynamic, which means that the only reliable time to validate user roles is at the time of key use.
NOTE The Trust Protection Foundation Master Admin and Code Signing Administrator roles cannot be assigned as Code Sign Manager - Self-HostedKey Users.
- Role members must be in groups. Checking this box disallows Owners from selecting individual users to fill roles in code signing. All roles must be assigned to groups.
- Wait period before timing out requests. Specifies the number of seconds to wait before the CSP will time out. This value is pushed from the Trust Protection Foundation server to the CSP clients.
The Request in Progress field provides Code Signing Administrators the ability to customize the dialog returned to the Key User when an approval is required or a signing operation is rejected.
EXAMPLE In the case where approval is required to use a code signing key, providing an email address for Key Users to get additional information may be helpful.
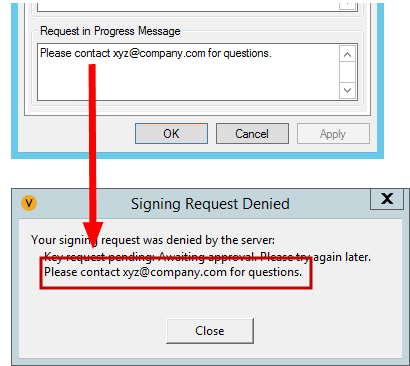
If you enter a message that contains the macro "$flowmessage$", only what you enter will be displayed, with "$flowmessage$" being replaced with the flow status.
EXAMPLE Using the "$flowmessage$" macro.
Details about code signing events are saved in the code signing archive, which you can search either in the Code Sign Manager - Self-HostedUI or through the audit API endpoints. By default, archive events are never deleted.
To delete archive events that are older than a set period, adjust the value in the Keep Sign Archive Entries for xx days field.
WARNING! All archive entries older than the number of days you set will be deleted.
To keep Code Sign Manager - Self-Hosted from creating new archive entries altogether, select the Disable Sign Archive checkbox. When the archive is disabled, any existing entries will remain in the archive, even if they exceed the period set using the Keep Sign Archive Entries option.
If the signing archive is currently disabled, you can enable it by deselecting the Disable Sign Archive checkbox.
NOTE About 1.6 GB of disk space is needed for every 10,000 signing archive events.
Disable JWK Public Keyserver
Starting the Code Signing Key Server component enables a JWK public key server and a GPG public key server. Checking the Disable JWK Public Keyserver checkbox disables the JWK key server but leaves the GPG key server active.
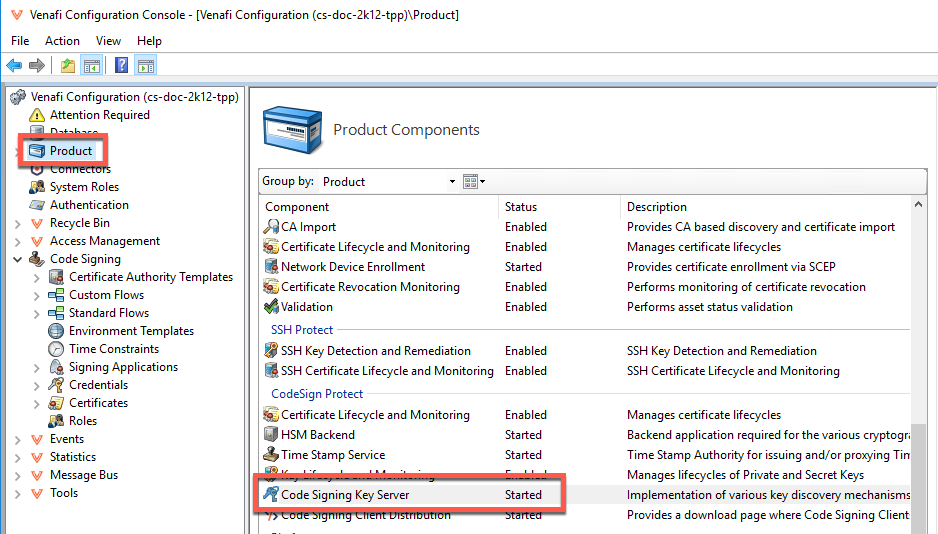
NOTE You can check if the Code Signing Key Server component is started by clicking the Product node in CyberArk Configuration Console and scrolling down to the Code Sign Manager - Self-Hosted section.
Certificate Configuration
If you want Owners to be able to add a SAN Email to certificate requests, check the Allow SAN Email checkbox.