SSH critical alerts widget
The SSH Critical Alerts widget helps you to identify risks before they become compromises. This is especially important in cases where the risk is high. For example, identifying public keys for which the corresponding private key cannot be located creates a high risk, especially when the key involves access to a server's root or administrative account.
SSH Critical Alerts widget
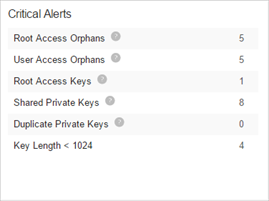
The SSH Critical Alerts widget provides immediate insight into the following threats:
- Root Access Orphans - A private key that is paired with a public key belonging to a root account is unknown or missing. These missing keys, known as root orphans, create high risk because the people who have the private keys could have unauthorized access to root accounts.
- User Access Orphans - A private key that is paired with a public key belonging to a non-root account is unknown or missing. These missing keys, known as orphans, create some risk because the people who have the private keys could have unauthorized access to non-root accounts.
- Root Access Keys - All key sets found in a root account at the server. Accessible root accounts create risk because no one should be allowed to log in to a root account with public key authentication.
- Shared Private Keys - Private keys that have duplicates owned by different users.
- Duplicate Private Keys - An unauthorized instance of duplicate private keys where a policy has been configured to prohibit private key duplication.
- Key Length < 1024 - Any asymmetric keys using an encryption length that is less that what you have specified in the associated policy. You can configure an SSH policy to bring keys in compliance with your key length requirements. For more information, see .