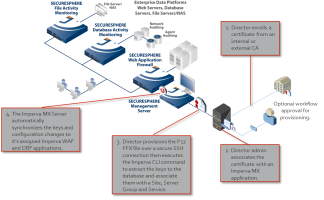
Imperva MX configuration
The CyberArk Trust Protection Foundation™ Imperva® MX driver supports provisioning of SSL certificate public and private key pairs to Imperva SecureSphere Management servers (MX) that synchronize to Imperva Web Application Firewalls (WAF) and Imperva Database Firewalls (DBF).
Imperva MX Driver Overview
The Imperva MX Driver provisions a public and private SSL certificate key pair to an Imperva Management Server on SecureSphere, version 9.5.
(Click image above to see a larger version. Click the image again to minimize it.)
The Imperva MX driver uses a P12 password protected PFX format and Imports the keys into the Imperva MX with the Imperva key tool using a temporary .csv file. The following attributes can also be configured in the driver and associated with the certificate key pair on the Imperva MX:
- Key Name
- Site
- Server Group
- Service
- HSM – True/False
- Temporary Random PFX filename
- Random Password for the PFX
Here is an example of the .csv content used to set the attributes for the key pair during provisioning:
These attributes coincide with the Imperva SecureSphere MX tree structure:
- Site (Folder folder: Datacenter or Location name)
- Server Group (One or more web server, referenced by IP, TCP port)
- Service (Web folders such as Apache, Tomcat, Websphere referenced by TCP port) / Application (Web app, referenced by URL or Hostname)
Here is another, more literal example:
- US-East
- company.com
- tomcat
- public-site
- partner-site
- webmail.company.com
- IIS
- OWA
- company.com
- EMEA
- company.de
- tomcat
- public-site
- company.de
File Naming
The Imperva MX driver manages the process of naming the keys as they are imported into the database. This is the best method for provisioning new and renewal certificate key pairs to the Imperva MX. This method is consistent with other Trust Protection Foundation provisioning drivers that control the file names. The public and private key pair is represented in the Imperva MX database with one key name. Automated key naming will be handled as follows:
Original common name:
www.qa.somedepartment.myreallycoolradicalawesomedomainthing.net
Trust Protection Foundation generated key name:
www.qa.somedepartment.myreallycoolradicalawesomedomainthing.net-446317BB00000012BF78-8BC8DB
Trust Protection Foundation also includes the certificate’s serial number and a six digit hash of the serial number to ensure uniqueness.
The Imperva MX has a 200 character file name limitation so it is doubtful any truncation will ever be needed for the common name. In the event it is needed the common name would be truncated from the permission most characters.
Known Limitations - No Post Provisioning Validation
Currently there is no Imperva CLI command to query the database that can be used in Trust Protection Foundation’s post provisioning process for onboard or network validation (compares what is on the Imperva database with the certificate in the Trust Protection Foundation's secret store.) The workaround for now is to turn off network and onboard validation in the Imperva MX driver settings.Venafi has requested from Imperva a CLI or API command to allow for validation; there is currently no availability date or commitment at this time.
TIP To browse topics in this section, use the menu on the left side of this page.