Scopes for token
An access token ties together the scopes and restrictions your integration needs to read or write, and interact with our products. First, in either the UI or using the Grant management endpoints, you set up and register scopes that your API client will use. For more information, see Setting up access token authentication.
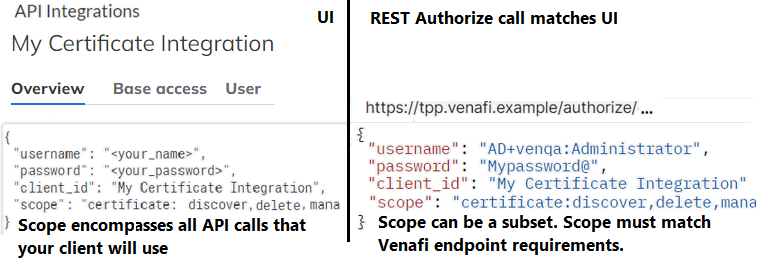
After setup, you get a token from an Authorize method, such as POST Authorize/OAuth. Use all or part of the scope that matches the API application (known as an integration in the UI). The integration JSON matches Trust Protection Foundation endpoints that your client will use. The token in the response goes in the header of each client API call. When your client completes its task, it can revoke its token.
- Scope
- A range of one more scopes that represent the set of API calls that a client will make. If the endpoint updates a resource, be sure to include the required restriction. The most commonly used scopes are listed below. However, the wizard can import any required scope:
Admin: API calls that help you manage the application. For example GET Log/LogSchema.
Agent: API calls that access to Agent resources. For example, GET Client/Details.
Certificate: API calls that manage certificates. For example, POST Certificates/Request.
Code Sign: Admin API calls to Code Sign Manager - Self-Hosted endpoints. For example, POST Codesign/CreateApplication.
Codesignclient: Code Sign Manager - Self-Hosted signing endpoints. For example, POST API/Sign.
Configuration: Basic management tasks that require policy, metadata, engine, or workflow. For example, POST Config/Find.
Restricted: Low level work such as SecretStore/LookupByVaultType.
Security: Credentials and permissions. For example, POST Credentials/Delete.
SSH: SSH key or certificate task. For example, POST SSH/KeysetDetails.
- Restriction
- The part of a scope that allows endpoints to update or change CyberArk resources. If the endpoint supplies read-only data, it may not have a restriction.
- Token
- The OAuth grant that allows the client application to make API calls. Requires an API Auth call that includes a scope parameter that matches API Application Integration wizard settings.
In the UI and the Authorize call, what scopes and restrictions do I use?
The UI values you specify are the same ones you pass in the Authorize scope parameter. You can specify basic scopes and restrictions based on the purpose of the integration. If the integration needs a specific grant, find the endpoint in the Scope map for tokens. Each endpoint also has a section in this guide that provides additional policy and role information.
|
Scope and Developer Example |
Privileges and Restrictions |
|||||
|---|---|---|---|---|---|---|
| Approve | Delete | Discover |
Manage |
Revoke |
[Other] |
|
|
admin |
|
|
|
|
|
recyclebin |
|
agent |
|
|
|
|
|
|
| certificate scope: certificate:approve,delete,discover,manage,revoke |
|
|
|
|
|
|
|
codesign scope: codesign:approve,delete,manage |
|
|
|
|
|
|
|
codesignclient |
|
|
|
|
|
This is a read-only privilege. |
| configuration scope: configuration:delete,manage |
|
|
|
|
|
|
| restricted scope:restricted:delete,manage |
|
|
|
|
|
|
| security scope: security:delete,manage |
|
|
|
|
|
|
| ssh scope: ssh:approve,delete,discover,manage |
|
|
|
|
|
|
| statistics (requires Vendor integration) scope:statistics |
|
|
|
|
|
This is a read-only privilege. |
|
(Read access) Specify a scope. (Many scopes) Use a semi-colon (;) |
|
|
|
|
|
|