Running an SSH discovery: finding devices and SSH keys
Discovery of devices and other security assets, such as SSH keys, happens when Server Agents that have been deployed to devices in your network receive work from Trust Protection Foundation.
Work is configured within Client Group Settings. Therefore, when you configure SSH discovery for a group, the next time agents check in with Trust Protection Foundation, the agent performs a scan on the device where it is installed and returns discovered assets, such as SSH keys, to Trust Protection Foundation.
Depending on how you configured those groups, SSH discovery occurs whenever installed Server Agents check in with Trust Protection Foundation. Agents check in according to the schedule you set up when you configured SSH discovery work. For more information, see Setting up SSH discovery work for Server Agents.
If you want to run SSH discovery at any time, make sure that you set the Scan Interval on the SSH Discovery tab to On Receipt, and then from a command line on a device where the agent is installed, run the following command:
vagent -m
Once executed—and assuming that SSH keys are found—you would see something similar to the following:
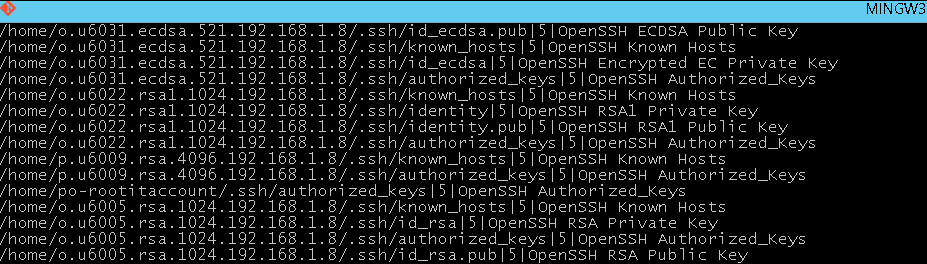
For more information about command line options, see Server Agent command line reference.
TIP To browse topics in this section, use the menu on the left side of this page.