SSL/TLS network validation
The CyberArk Trust Protection Foundation™ validation feature validates your encryption system certificates and applications to determine if the correct certificate is being used. It also determines if it is functional and if it is installed in the correct place on its associated platform or keystore.
Security, compliance, and technological innovation have introduced new criteria for the validation of certificates and the servers that host them.
Trust Protection Foundation offers certificate validation that is easy to use, provides more actionable results, helps assure compliance with industry standards, and supports best security practices.
- You can configure validation and see results in Certificate Manager - Self-Hosted.
- When you view validation results, you can clearly see every target that was scanned for the certificate.
- Validation provides complete, qualitative analysis of the certificate chain presented by the hosting server.
- Validation identifies the SSL or TLS protocols that the hosting server supports. CyberArk provides these communication protocols: SSL 2.0, SSL 3.0, TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3.
- Different certificates that are hosted on the same IP address and port can be validated.
Network Validation workflow
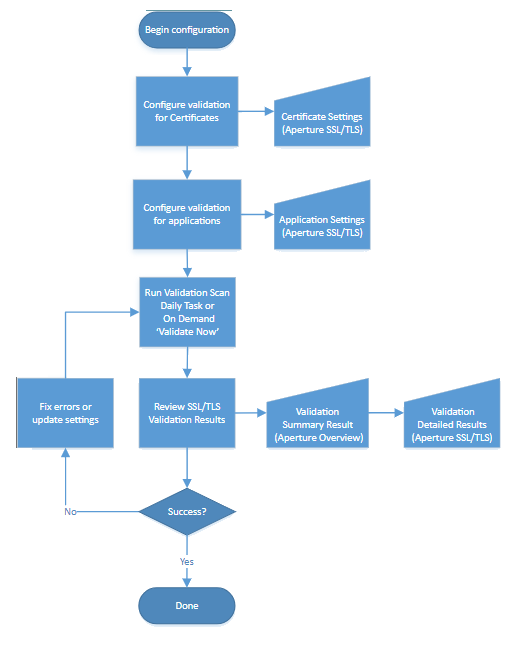
TIP Each square in the diagram has a corresponding topic in the side navigation menu.
How Network Validation works
|
Network Validation |
|
|---|---|
|
What it validates |
SSL/ TLS application objects and certificates |
|
What it's looking for |
Certificate is functional Correct certificate is being used |
|
How it works |
If the server responds to SSL/TLS request, Trust Protection Foundation knows the certificate is functional. When certificate's serial number is retrieved and compared, Trust Protection Foundation can determine if the correct certificate is being used. If Use Certificate Common Name is enabled, Trust Protection Foundation does a DNS lookup of the certificate's common name then validates the certificate at every IP address returned. Results are reported individually. If you enable Network Validation on the Application object, Trust Protection Foundation validates the certificate associated with the Application object. |
TIP To browse topics in this section, use the menu on the left side of this page.