Enabling and configuring ACME using TLS Protect
You can enable and configure the ACME service using TLS Protect.
NOTE Before you do this, make sure that the ACME server component is installed. See Installing the ACME Service.
To enable and configure ACME
-
From the TLS Protect menu bar, click Configuration> ACME.
-
You will be prompted to Enable ACME?. Click Yes.
-
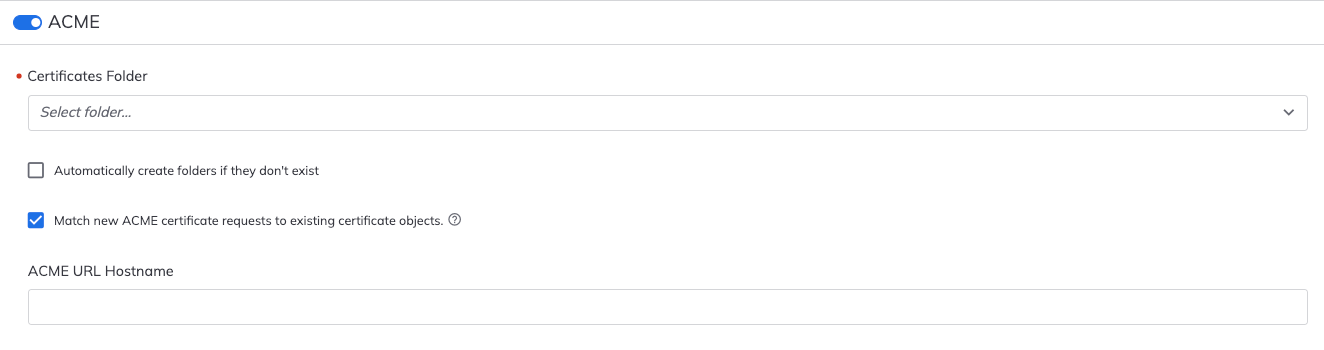
Under Create Certificates in, select the folder into which ACME Service certificates will be placed.
IMPORTANT A CA template must be assigned to the folder that you select. See Assigning a CA template to a policy folder.
Also, make sure user accounts have Create and Write permissions to the new sub-folders where certificates will be created and stored. If permissions are not correctly set and the user tries to create a certificate in the folder, an error message saying
ACME - Insufficient Permissionsis written to the log file. -
(Optional) Select Automatically create folders if they don't exist.
- When selected, if a folder doesn't exist when the certificate's location is specified, a folder with that name will be created. In the certbot request's URL, the new folder's name cannot contain uppercase letters.
- When cleared, certificate requests will fail if the folder doesn't already exist. An error message will be sent via certbot and an event will be logged in Trust Protection Platform. Certbot will display a similar message in the letsencrypt.log file.
-
Match new ACME certificate requests to existing certificate objects. (Enabled by default for new installations)
- When selected, new ACME certificate requests will be matched via the SAN(s) and placed as the active certificate in the matched certificate object. The active certificate is then placed in the previous versions / history tab of the certificate object. This also changes the certificate object naming pattern for the new certificate object so it no longer contains a unique time stamp but contains only the first domain from the request. Matching will be applied only if the renewal request comes from the same account that requested the initial certificate; otherwise, a new certificate object will be created.
-
When cleared, new ACME certificate requests will create new certificate objects without matching to existing certificate objects. The certificate objects naming pattern will contain the first domain from the request and a unique time stamp.
-
For these settings to take effect, Internet Information Server (IIS) must be reset.
NOTE Renewals may incur additional charges. If the Certificate Authority supports re-issuance, the renewal requests may be handled as a re-issuance or as a replacement. This can lead to the Certificate Authority revoking the historical certificate.
-
Type the ACME URL Hostname.
NOTE The default name is the fully qualified domain name (FQDN) of the engine. You have the option to change it here.
- When you're done, click Save.
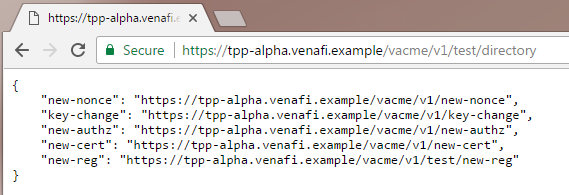
In a web browser, type https://[ACME_server_FQDN]/vacme/[v1|v2]/[TPP_folder]/directory
For example:
https://tpp-alpha.venafi.com/example/vacme/v1/test/directory
The displayed text confirms that the ACME server is working. You can also see the URLs that the ACME client will use (internally) to register and request certificates.
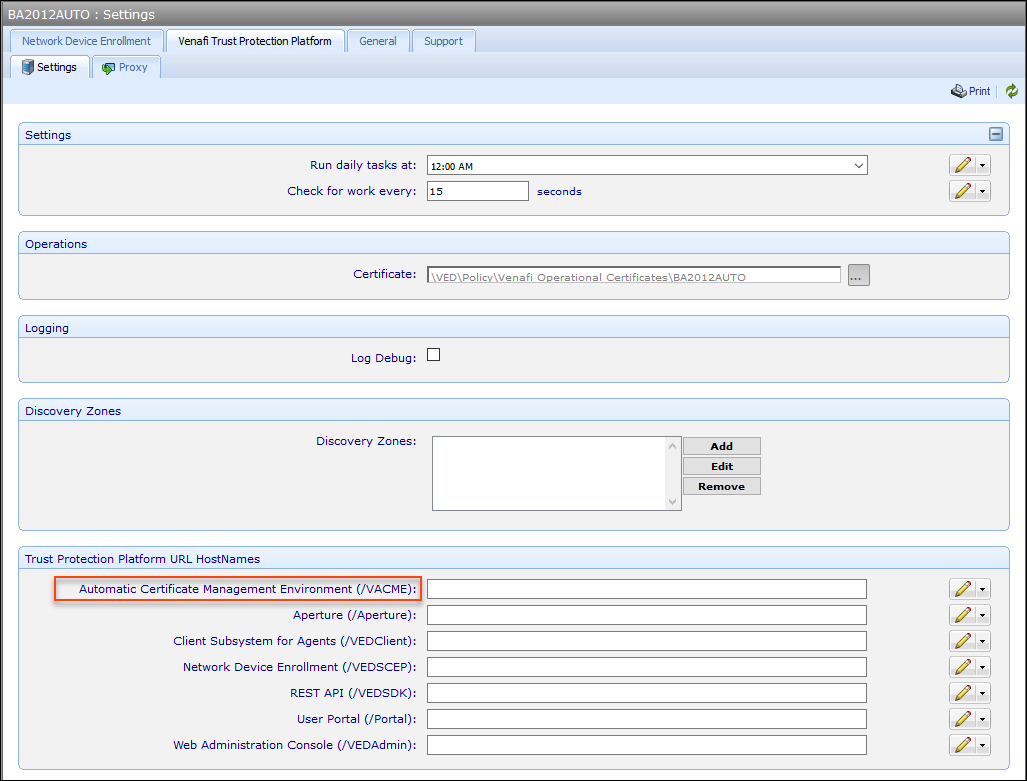
- In Policy Tree, go to the Platforms tree.
- In Platforms, click an Engine name.
-
Under Trust Protection Platform URL HostNames, in the Automatic Certificate Management Environment (/VACME) field, enter the hostname of the ACME server.
NOTE The default name is the fully qualified domain name (FQDN) of the engine.
- Click Save.