PowerShell script reference for Adaptable CA
This section contains all available PowerShell functions for use with the Adaptable CA driver. PowerShell scripts are stored in the Program Files\Venafi\Scripts\AdaptableCA folder. However, the sample DigiCert PKI Platform.ps1 is included in the \Venafi\Scripts\AdaptableCA\Samples folder.
For more information about the sample script, see Using the sample DigiCert PKI Platform PowerShell script.
NOTE To work effectively with any CyberArk adaptable solution, you must have some working knowledge of PowerShell scripting, or you must have equivalent experience with a scripting language similar to PowerShell.
The following diagram shows which PowerShell functions are invoked at which stage in the certificate lifecycle:
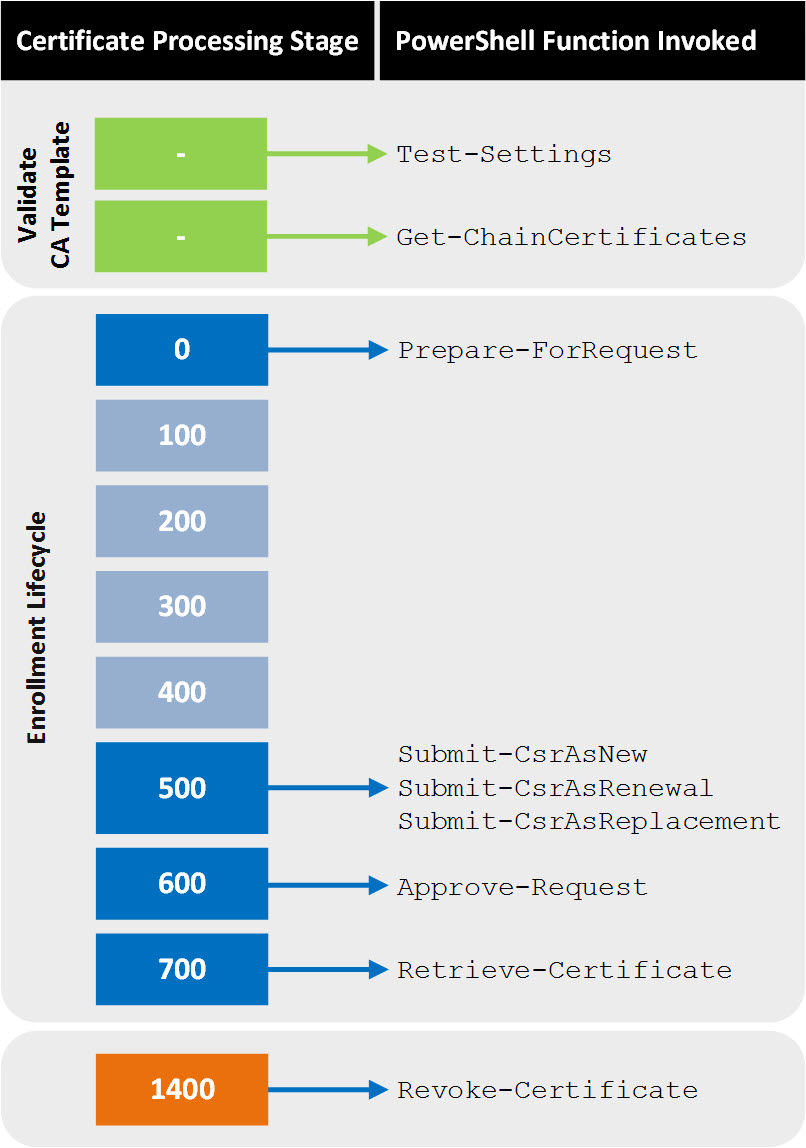
For information about processing stages, see About certificate lifecycle management.
BEST PRACTICE When customizing (or creating a new) PowerShell script, keep the following security best practices in mind:
- Avoid hard-coding credentials into your PowerShell scripts.
- Only include code in functions that relate to the task they are designated to perform.
- Scripts should not do anything that could alter the integrity or availability of the local Windows system (the system that is hosting Trust Protection Foundation).
About debug logging
When a user has requested debug logging by checking Enable Debug Logging for Adaptable Flow<Venafi Home>\Logs directory by default (e.g. C:\Program Files\Venafi\Logs).
For information about where Enable Debug Logging is configured for Adaptable FlowAdaptable CA, see
Variable reference
|
Variable Name |
Data Type |
Description |
|---|---|---|
|
AuxPass |
String |
The password portion of the Secondary Credential when a user name or a password credential is assigned, or the PKCS#12 password when a certificate credential is assigned |
|
AuxPfxData |
Byte Array |
A PKCS#12 byte array that contains a client certificate and private key when a certificate credential is assigned as the Secondary Credential |
|
AuxUser |
String |
The user name portion of the Secondary Credential when a user name credential is assigned |
|
CertObjDN |
String |
CyberArk distinguished name (DN) of the certificate object in the policy tree |
|
CustomFields |
Hashtable |
Hash table keys are Custom Field labels and the values are strings (single-valued) or string arrays (multi-valued). |
|
OAuthAccessToken |
String |
OAuth token passed to the PowerShell script. Tokens are passed only after you've provided the required information in the WebSDK OAuth Token Configuration settings of the Adaptable object. See Configuring the Adaptable CA object. How it worksWhen used, each time your script is called, Trust Protection Foundation requests a new token automatically. Each new token is associated with both the specified user and with the referenced application ID. After the script finishes running, Trust Protection Foundation revokes the token automatically. To get started, see Adaptable CA prerequisites. |
|
PfxData |
Byte Array |
PKCS#12 keystore containing client certificate and private key for authenticating with the CA; this and the PfxPass are used together to instantiate an X509Certificate2 object for client certificate authentication. |
|
PfxPass |
SecureString |
Password for access to the private key of the PfxData PKCS#12 |
|
UserName |
String |
User name for authenticating with the CA |
|
UserPass |
String |
Password for authenticating with the CA |
|
WebSdkUrl |
String |
String representing the fully-qualified domain name to the WebSDK of your Trust Protection Foundation server. For information on where this variable data is set, see Trust Protection Foundation server configuration. |