Managing encryption keys in the Policy tree
In the Policy tree, object encryption is managed via policy. In the Policy object configuration, you can determine which encryption keys are used to secure which types of objects. For example, in the Policy object’s SSH User Key tab, you can select the encryption key used to secure the policy’s subordinate SSH User keys. Likewise, in the Policy object Certificate tab, you can select the encryption key used to secure the private keys associated with the policy’s subordinate Certificate objects.
IMPORTANT The Default Encryption Key settings in the Policy object apply only to subordinate objects in the Policy tree. To define default values for Credential objects in the Credentials tree, you must define the Default Encryption Key settings in the Root Credential object. For more information, see Managing encryption keys in the Credentials Tree.
The following two sections review how to manage encryption keys in the Policy tree.
In the Policy tree, folder are used manage which encryption keys are used to encrypt which types of encryption assets.
-
From the Platform menu bar, click Policy Tree.
You must have the View and Write permissions to the Policy object to define Policy’s default encryption keys.
- In the Policy tree, select the Policy object where you want to configure object encryption keys.
-
In the Policy object configuration, go to the object configuration tab for the type of object you want to encrypt.
The following table identifies where you can configure the encryption key for each type of encryption asset:
Policy Object Encryption Key Settings To Encrypt:
Go To:
Certificate Private Keys
Policy > Settings > Certificate tab
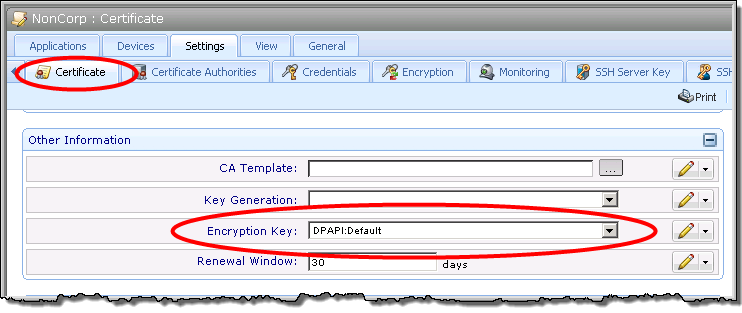
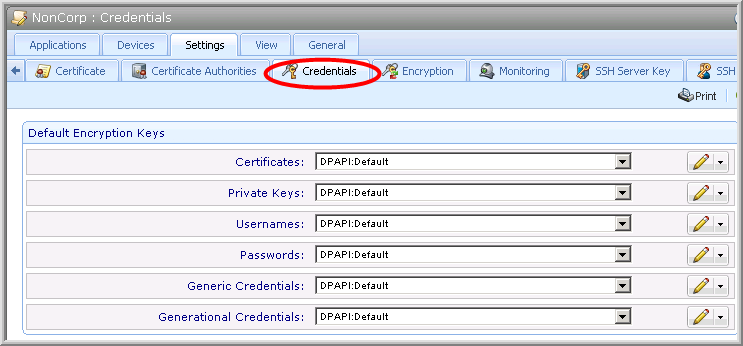
Credential Objects
Policy > Settings > Credentials tab
The Credentials tab allows you to assign an encryption key to each type of Credential object: Certificate, Private Key, Username, Password, Generic, and Generational. For more information on Credential objects, see Working with system credentials.
-
(Optional) Click the
 icon to lock the Encryption Key values.
icon to lock the Encryption Key values.When you lock an Encryption Key value, Trust Protection Platform uses only the selected encryption key to secure all subordinate objects of that type.
- Click Apply/Save.
You can view the encryption keys used to secure a Policy’s subordinate objects from the Policy object’s Encryption tab.
To view the encryption keys used to secure a policy’s subordinate objects
-
From the Platform menu bar, click Policy Tree.
You must have the View and Write permissions to the Policy object to define Policy’s default encryption keys.
- In the Policy tree, select the Policy object where you want to view object encryption keys.
- In the Policy object configuration, go to the Settings > Encryption tab.
-
Click Load Key Data.
Trust Protection Platform displays the policy’s subordinate certificates, SSH keys, and credentials and their associated encryption keys.
