Rotating encryption keys for a policy or ObjectDN
Trust Protection Platform maintains all system information—that is, configuration settings, managed server and certificate information, credentials, SSH server and private keys, and archived certificates—in a database. To secure this information, Trust Protection Platform uses either a software encryption key, a hardware encryption key in a supported HSM, or both to encrypt sensitive information used to connect to the database. Organizations that must periodically rotate their encryption keys can easily do so. After the migration, administrators can verify that all secrets have been re-encrypted with the new encryption key.
Encryption key migration can be handled globally via the Root Encryption Driver object, or it can be handled at the Policy level for the Policy’s subordinate objects.
Global key rotation is done in the Venafi Configuration Console. For more information on how to rotate all encryption objects in Trust Protection Platform, see Rotate Secret Store encryption keys.
To rotate encryption keys for a specific Policy object
-
From the Platform menu bar, click Policy Tree.
IMPORTANT You must have master administrator permissions to the root Encryption Driver object. Administrators with Delete permissions to a specific encryption key can also rotate encryption away from that key.
NOTE This option is provided so that administrators can rotate encryption away from an encryption key before they delete the associated Encryption key object.
- In the Policy tree, select the Policy object whose encryption keys you want to rotate.
- Select the Settings > Encryption tab.
-
Click
 Load Key Data to display all subordinate objects currently encrypted with an encryption key.
Load Key Data to display all subordinate objects currently encrypted with an encryption key. The Encryption tab lists all subordinate objects with an Encryption attribute, even those objects whose encryption is currently set to Null (no encryption).

-
Click
 Rotate.
Rotate.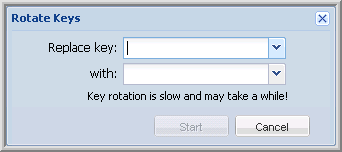
-
In the Replace key field, designate which encryption key you want to replace.
Encryption is rotated away from this key. All of the policy’s subordinate objects currently encrypted with this key will be re-encrypted with the new key.
-
In the With field, designate the new encryption key you want to use.
Encryption is rotated to this key. All of the policy’s subordinate objects currently encrypted with the designated replace key will be re-encrypted with this key.
-
Click Start to rotate the encryption keys.
All of the policy’s subordinate objects currently encrypted with the designated Replace key are re-encrypted with the new key. This includes certificates, private keys, SSH keys, symmetric keys, and all credentials.
NOTE By default, public information such as certificates and public keys are not encrypted. If you rotate the Null key, Trust Protection Platform re-encrypts all objects—even public information—with the new key. Encrypting public information may add unnecessary processing overhead and, depending on the number of objects in your tree and whether your encryption keys are stored on an HSM device, may impact system performance. If you want to rotate encryption for public information such as certificates and public keys back to a Null value, please contact Venafi Support.