Request Identifier Fields tab
The Request Identifier Fields options allow Code Signing Administrators to determine which attributes of a signing request are used to match previous signing requests that are not yet complete. These global settings can be overridden in Environment Templates.
Every code signing private key managed by Code Sign Manager - Self-Hosted is associated with an Environment, and each Environment has an associated Flow. The final step in every Flow is to sign the code. In some cases, a signing request's Flow cannot finish in a single operation, such as in the case of a required approval.
When you submit a signing request, the values from the request identifier fields are hashed to create a unique request identifier. This request identifier is used to determine if the request is a new request or a continuation of a previous request that is awaiting approval.
If the identifier doesn't match any existing identifier for requests in the Pending Approval or Active Approval states, it is considered a new request and will start at the beginning of the Flow that is associated with the Environment. If the identifier does match an existing identifier, then it is considered a continuation of an existing request.
When a Key Use Approver approves a signing request, they will see both the request identifier as well as the request identifier fields, as shown in the screenshot below:
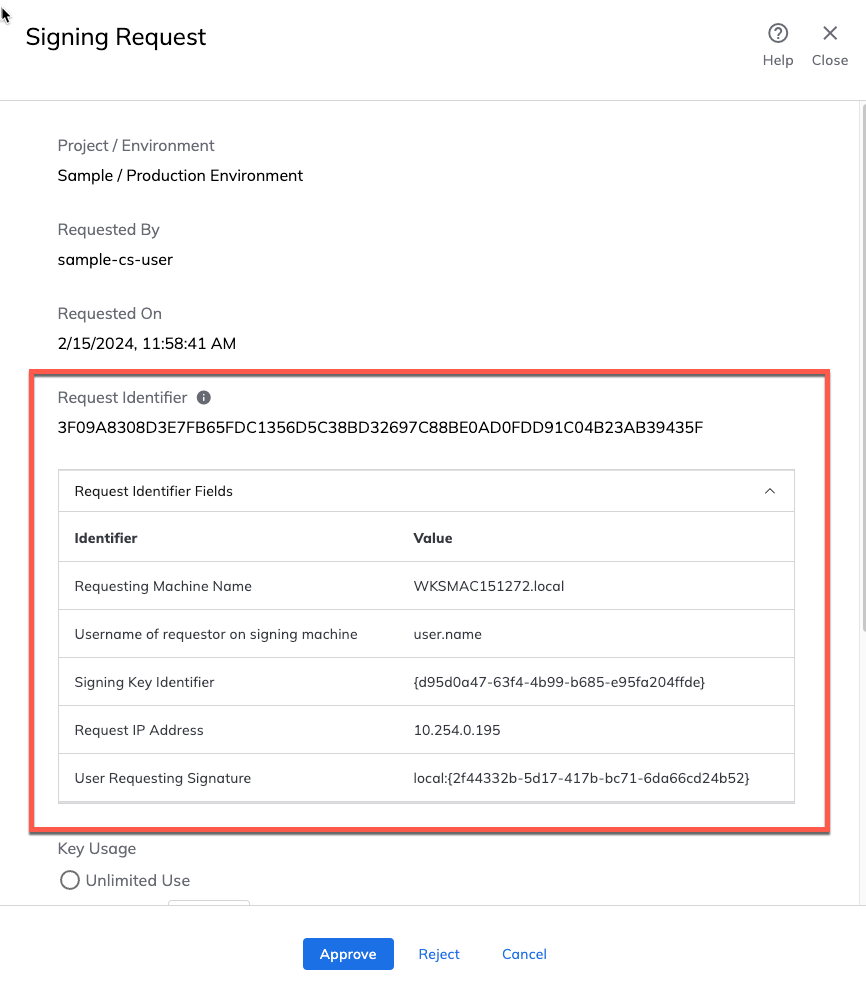
To learn more about Flows, see Create Flows.
The following values can be used to match signing requests with previously-submitted requests that are not yet fulfilled. By default, the following fields are selected:
-
Command Line
-
Signing Key Identifier
-
Requesting Machine Name
-
Username of requestor on signing machine
CAUTION Changing these options invalidates any existing pending approvals.
|
Identifier |
Description |
|---|---|
|
Command Line |
The actual command used to issue the signing request. This is enabled by default. This identifier should be disabled for GPG Environment Templates that use a Flow with approvals. |
|
Signing Executable |
The filename of the signing application. |
|
Signing Executable Checksum (Hash) |
The hash of the signing application being used to sign. |
|
Signing Executable Signer |
The signer of the signing application. This is the subject of the certificate used to sign the signing application itself. |
|
Signing Executable Size |
The disk size of the signing application. |
|
Request IP Address |
The IP address of the workstation from which the request was issued. |
|
Request Justification |
The request justification is a freeform field that allows the Key User to include a reason why they are requesting use of the key. |
|
Signing Key Identifier |
The Trust Protection Foundation unique identifier for a private key. This is enabled by default. |
|
Requesting Machine Name |
The name of the workstation from which the signing request is made. This is enabled by default. |
|
Data to be signed |
The hash of the data (such as an executable, macro, or document) that the signing application creates. NOTE Checking this option ensures that the binary being signed cannot change between the request, approval, and signature. |
|
User requesting signature |
The Trust Protection Foundation username of the user requesting the signing. |
|
Username of requestor on signing machine |
The workstation username of the user requesting the signing. This is enabled by default. |