Configuring an HTTP proxy
Trust Protection Foundation respects a system proxy configured in Internet Explorer, which should be set for the user account under which the service is running. At the root of the Platforms tree, you can configure a single proxy to be used by all Trust Protection Foundation engines and HTTP-based services. If your organization has multiple proxies, we recommend that you set the most used proxy address at the top of the Platforms tree and then override that setting with a different address on individual Trust Protection Foundation engines.
A proxy can be configured on an individual Trust Protection Foundation engine if the proxy setting at the root of the Platforms tree has not been locked. Setting a proxy configuration on an individual Trust Protection Foundation engine overrides the value set at the root of the Platforms tree.
JWT Mappings operate in tandem with the central proxy configurations set at the root of the Platforms tree. See About JWT Mappings.
CyberArk Trust Protection Foundation - Self-Hosted and the Amazon AWS SDK use the System.Net.HttpWebRequest class, which uses the Microsoft Crypto API to perform revocation checking as part of the SSL/TLS handshake. The MS Crypto API must be configured to use the proxy during revocation checking so that these requests will be performed through the proxy as well.
You may see this issue with any CyberArk Trust Protection Foundation - Self-Hosted driver, or in some other areas of CyberArk Trust Protection Foundation - Self-Hosted. For more information see the following Microsoft documentation:
-
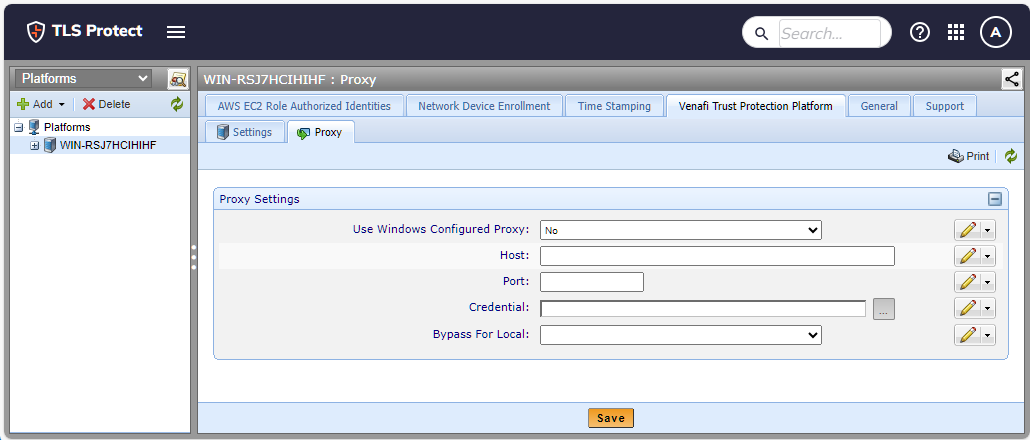
From the Platform menu bar, click Policy Tree.
- Select the Platforms tree from the Tree drop-down menu.
- Select the root of the Platforms tree.
- Select the Platforms tab, and then click Proxy.
-
Configure the proxy settings.
TIP To prevent a proxy from being set on an individual Trust Protection Foundation engine, lock the proxy settings at the root of the Platforms tree.
-
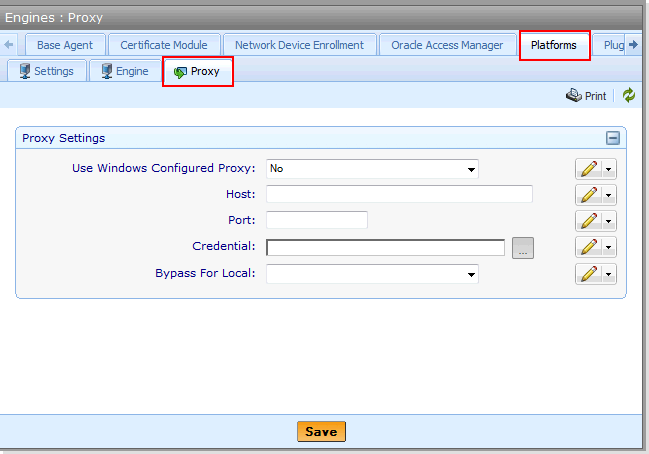
From the Platform menu bar, click Policy Tree.
- Select the Platforms tree from the Tree drop-down menu.
- Select theTrust Protection Foundation engine that will hold the settings.
- Select the CyberArk Trust Protection Foundation tab, and then click Proxy.
-
Configure the proxy settings.