Permission inheritance and flow down
Permissions flow down the tree. This means that when you grant permissions to an object, all subordinate objects inherit those same permissions unless you explicitly grant permissions to objects further down the tree.
Therefore, permission inheritance works as follows:
- Group permissions flow down the tree to all members of the group unless overridden by User or Group permission assignments further down the tree. Group permissions are additive.
- User permissions have the highest priority. User permissions override Group permissions assigned higher in the tree, but they are added to Group permissions granted further down the tree. User permissions can be overridden only by granting different User permissions further down the tree.
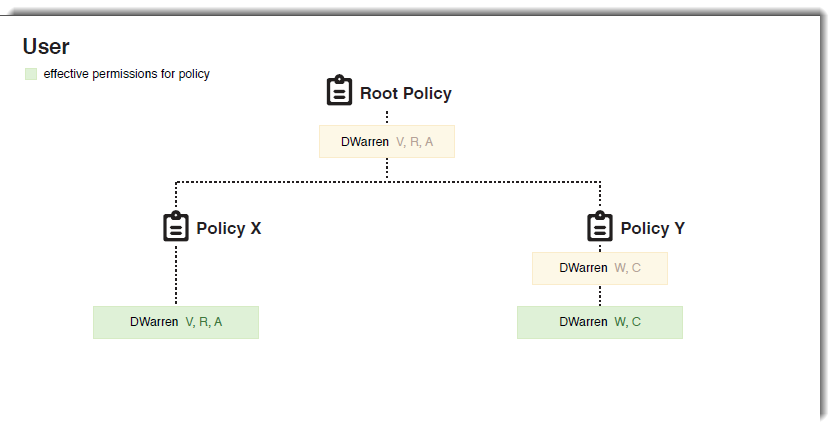
- DWarren - For Policy X, permissions of V, R, and A flow down from the Root Policy to Policy X.
- DWarren - For Policy Y, permissions were reassigned at Policy Y. Even though the Root Policy grants V, R, & A, the user permission reassignment at Policy Y overrides the Root Policy permissions.
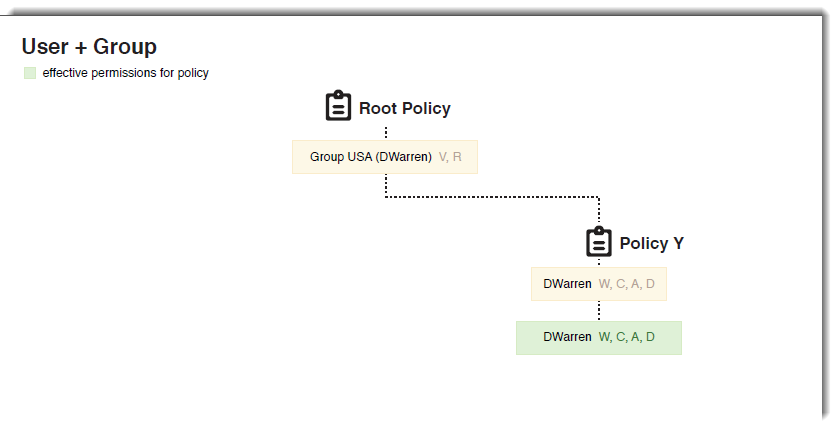
- DWarren - Group USA permissions at the Root Policy grants DWarren permissions V and R.
- DWarren - User permissions of W, C, A, and D are granted at Policy Y.
User permissions override Group permissions giving DWarren effective permission to Policy Y of W, C, A, and D.
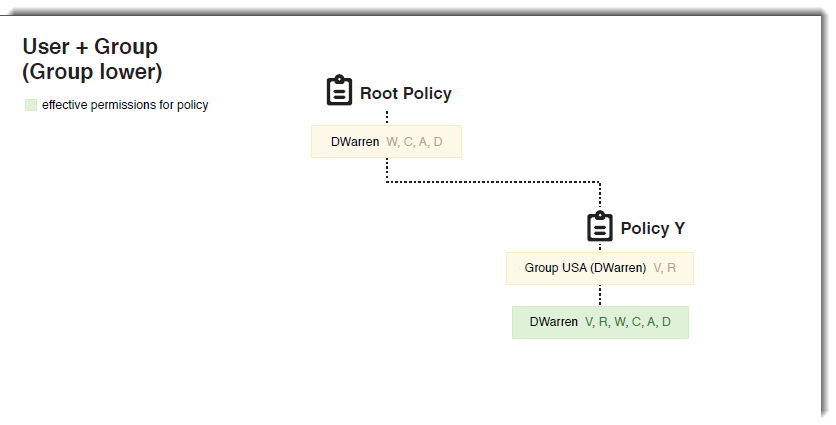
- DWarren - User permissions of W, C, A, and D are granted at the Root Policy
- DWarren - Group USA membership adds V and R to his permission set
Since Group permissions are additive, DWarren's effective permissions for Policy Y are V, R, W, C, A, and D.
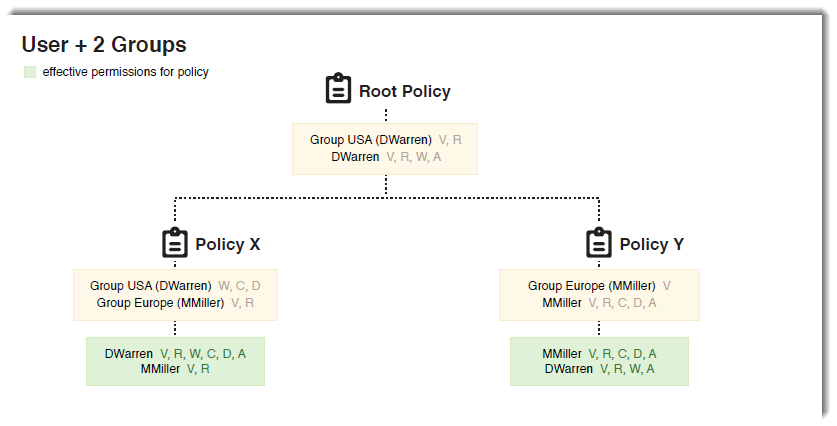
- DWarren has User permissions of V, R, W, and A and Group permissions of V and R at the Root Policy. Group USA gives him additional permissions of W, C, and D for Policy X. DWarren's effective permissions for Policy X are V, R, W, C, D, and A.
- MMiller has User permissions of V, R, C, D A for Policy Y. Group Europe grants him the permission of V. MMiller's effective permissions for Policy Y are V, R, C, D, and A.
For Policy X, User and Group permissions are combined when Group permissions are further down the tree.
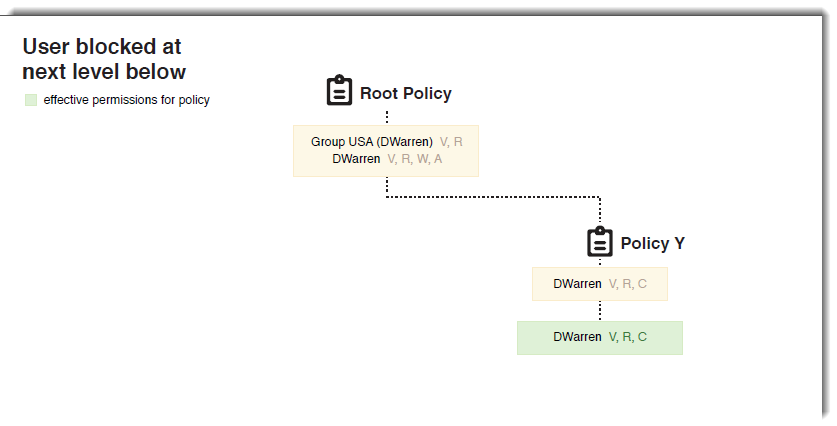
- DWarren - User permissions of V, R, W, and A are granted at the Root Policy
- DWarren - User permissions of V, R, and C are granted at Policy Y.
Since his user permissions were reassigned at Policy Y, permission A that was granted by the Root Policy is effectively blocked.
NOTE The Create permission implies View.
The Write permission implies Read.
The Manage Policy permission implies Read, Write, and Revoke but does not imply View. Users should be granted the View permission as well.
To see which permissions are assigned to a particular user or group, run an Entitlement Report.