POST Authorize/Integrated
Authenticates a user with Integrated Windows Authentication. Authorize/Integrated requires setup. After this call completes, place the access_token in the header of your REST call. Your client can reuse the same token until it expires. As necessary, your client should track the expiration time and use the refresh token to get a new one. On exit, your client can revoke the token.
DID YOU KNOW? This call, which is managed by the VEDauth service, replaces a Web SDK call by the same name.
CAUTION Secure your bearer tokens. Do not share tokens with other integrations. When processing completes, your integration can manage the grant by calling GET Revoke/Token.
Prerequisites
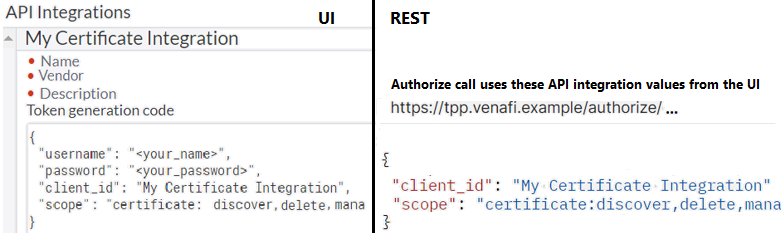
Register an API Integration and give the caller access. Use the scope and other information from the integration. For more information, see Setting up access token authentication.
Requirements
Permissions: The caller is not required to have any special permissions.
Headers
Content type: Content-Type:application/json.
- No bearer access token is necessary for this API call.
Parameters
To perform the initial server challenge, your REST API tool may require special NTLM authentication settings. For example, in the Postman Auth tab, you add the same credentials that appear in the JSON body.
In the request URL, specify vedauth. For example, POST https://tpp.venafi.example/vedauth/authorize/integrated. All parameter names are case sensitive.
Name | Description |
|---|---|
| client_id | Case sensitive. The value must match the Client ID in the API integration. For more information, see Setting up access token authentication. |
scope | The set of scopes and restrictions for the client_id. The set must:
|
state | (Optional) A session state, redirect URL, or random string to prevent Cross-Site Request Forgery (CSRF) attacks. |
| username | The API caller's username, which is already set in the local, AD, or LDAP identity provider. Valid formats:
|
Returns
Name | Description |
|---|---|
HTTP 200 | For valid requests, Authorize/Integrated returns a HTTP 200 message; and the following data:
|
HTTP 400 | If the response is HTTP 400, a generic error appears with a customized description for this particular endpoint.
|
HTTP 401 | If the refresh fails, this API call returns a HTTP 401; it includes one of the following:
|
Example: Get a Trust Protection Foundation bearer token
Request
POST https://tpp.venafi.example/vedauth/authorize/integrated { "client_id":"client-Integrated-auth", "scope":"Certificate:discover,manage,delete" }
Response
HTTP/1.1 200 OK
{
"access_token":"zmbVaygOBFtFV8TlUW9lqg==",
"refresh_token":"HKBOMauZqglTwy2odNKlCw==",
"expires_in":7775999,
"expires":1618855359,
"token_type":"Bearer",
"scope":"certificate:discover,manage,delete",
"identity":"local:{de3944a8-3479-4450-b412-0dacd642017d}",
"refresh_until":1642615359
}