POST SSH/AddAuthorizedKey
Creates an OpenSSH Authorized key for provisioning to a device. Authorized keys specify users who are allowed to log into a server using public key authentication in SSH. The SSH/AddAuthorizedKey API returns immediately after adding the key recorded to the Trust Protection Foundation database. This method does not wait until the key is actually provisioned on the specified device, which can take time depending on configured Agent schedule. To track the progress of key operations, call POST SSH/KeyDetails.
The key algorithm and length are taken from the SSH policy of the device folder. If the Algorithm is empty, the default is RSA. If the Key Size is empty, the Length is 2048.Requirements
- Token scope: SSH:Manage
Headers
Content type: Content-Type:application/json.
- Token: The bearer access token that you received. For example, Authorization:Bearer 4MyGeneratedBearerTknz==. For more information, see Passing a bearer token in your API calls.
Parameters
Name | Description |
|---|---|
AllowedSourceRestriction (Optional) | A list of allowed source restrictions for the key. If omitted, the value is taken from device policy. |
DeniedSourceRestriction (Optional) | A list of denied source restrictions for the key. If omitted, the value is taken from device policy. |
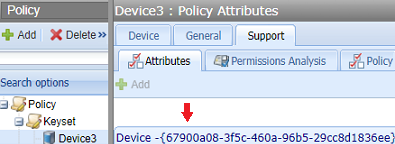
DeviceGUID | The GUID that identifies a device. Depending on your environment, the GUID may be expressed with or without curly braces {}. For example, {3d6b61d-1c71-4603-883f-25b8c2ceecdd}. To get the GUID, use POST SSH/KeysetDetails or the UI. For example:
|
Filepath | The path of the Authorized key file that contains the key. |
ForcedCommand (Optional) | The forced command for connections with the key. If omitted, the value is taken from device policy. |
Format (Optional) | The format of the SSH key. Can be omitted if the format is specified on device policy. Valid formats: OpenSSH, PuTTY, SSH2, or Tectia. |
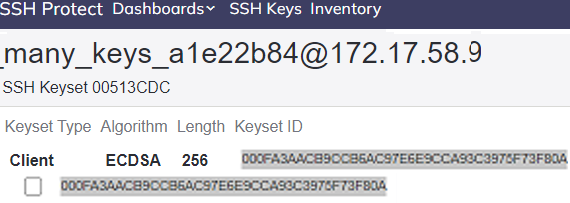
KeysetId | The identifier of a set of public and private key pairs. Depending on your environment, the value may be expressed with or without curly braces {}. You can get the KeysetId, from POST SSH/KeyUsage or the SSH Keyset Inventory. For example:
|
Options (Optional) | List of authorized key options. If omitted, the value is taken from device policy. |
Username | The user name of the owner of the key; |
Returns
Name | Description |
|---|---|
KeyId | Identifier of newly created key. The identifier for a set of public and private keys. The value is hexadecimal. If there is no private key password, the format is EncryptedPrivateKey-[unique number]. For example, EncryptedPrivateKey-3. |
Response | SshWebResponse object with result of the operation. For more information, see SSH SshWebResponse object. |
Example: Add an authorized key
Request
POST https://tpp.venafi.example/vedsdk/SSH/AddAuthorizedKey
Authorization:Bearer 4MyGeneratedBearerTknz==
{
"DeviceGuid":"{21a8574c-f448-4a8c-aa13-cbd6a07df49b}",
"Username":"user",
"Filepath":"/home/user/.ssh/authorized_keys",
"Format":"OpenSSH",
"KeysetId":"953C85736E1D254E60AB4F8665239D942157FAF6"
}Response
HTTP/1.1 200 OK
{
"KeyId":"143",
"Response":{
"Success":true
}
}