CodeSign Protect user and task flow
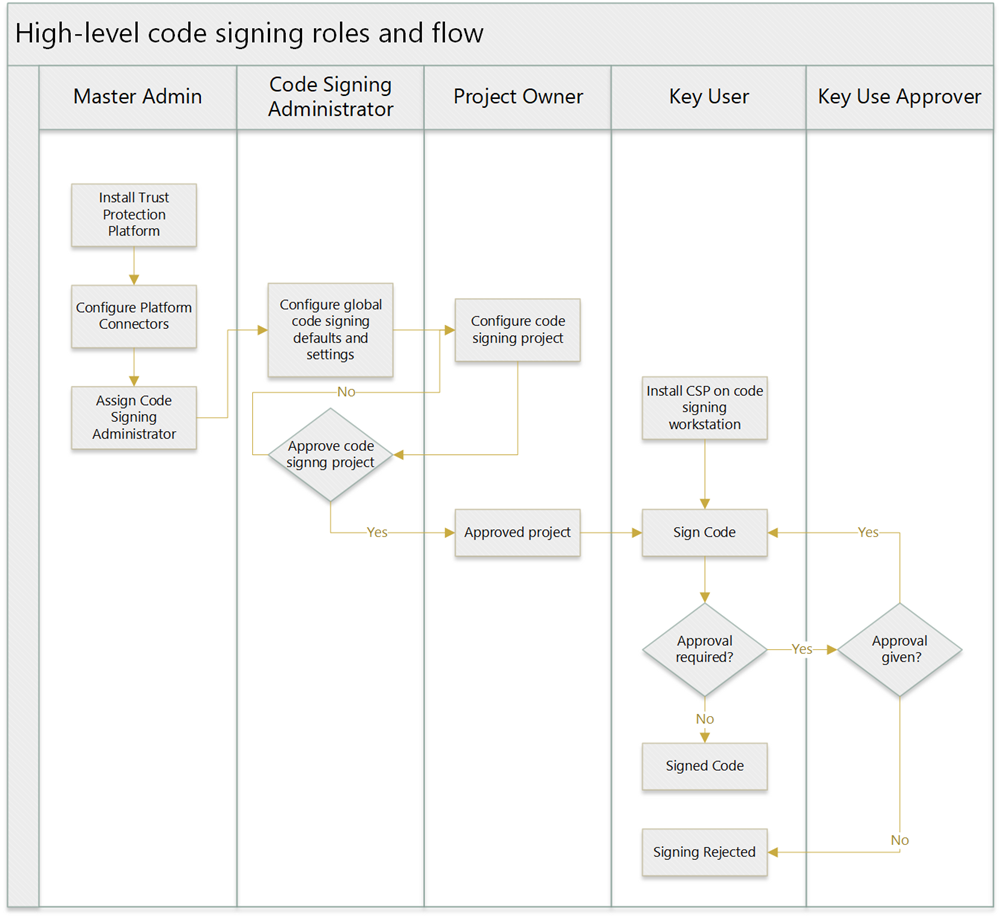
In order to secure the use of private code signing keys, Venafi CodeSign Protect has the ability to distribute responsibilities across a number of user roles. The following flowchart provides an overview of the Venafi CodeSign Protect process and describes which role is responsible for each high-level step in the process.
Each step in the flowchart has one or more tasks associated with it, which are detailed below the flowchart. To jump directly to the details about a step, click that step in the flowchart.
Install Trust Protection Platform
| Performed by | Master admin |
|
Interface |
Venafi Trust Protection Platform installation wizard |
|
Tasks |
Configure Trust Protection Platform connectors
| Performed by | Master admin |
|
Interface |
Venafi Configuration Console |
|
Tasks |
Assign Code Signing Administrator
| Performed by | Master admin |
|
Interface |
Venafi Configuration Console |
|
Tasks |
Configure global code signing settings
| Performed by | Code Signing Administrator |
|
Interface |
Code Signing MMC Snap-in |
|
Tasks |
Configure code signing projects
| Performed by | Owner |
|
Interface |
CodeSign Protect web interface |
|
Tasks |
Approve code signing projects
| Performed by | Code Signing Administrator |
|
Interface |
CodeSign Protect web interface |
|
Tasks |
Install the CSP on code signing workstations
| Performed by | Key Useror IT department |
|
Interface |
Venafi CSP installation wizard |
|
Tasks |
Sign code
| Performed by | Key User |
|
Interface |
Standard signing applications |
|
Tasks |
Sign code with existing signing applications using certificates managed by Trust Protection Platform. |
Approve use of private key
| Performed by | Key Use Approver |
|
Interface |
CodeSign Protect web interface |
|
Tasks |