Creating an IBM WebSphere DataPower application object
To enable Trust Protection Foundation to manage certificates and keys installed on DataPower Gateways, you must configure the DataPower application object. This object provides the information Trust Protection Foundation needs to monitor, enroll, or provision certificates and keys on its associated devices.
BEST PRACTICE Consider managing object settings using a policy. For more information, see
DID YOU KNOW? When you add an installation to a certificate, you'll have the option of defining (and editing) this object during that process, which means that you don't have to log in to Policy Tree as the following procedure describes. And because the settings are the same, you can use this topic for information about each setting.
For more information, see Creating a certificate installation.
To create and configure an IBM DataPower application object
-
From the Certificate Manager - Self-Hosted menu bar, click Policy tree.
- In the Policy tree, select the device object to which you want to add the new application object, and then click Add > Application, and then select DataPower.
-
When the new application object page appears, then under Status, clear the Processing Disabled checkbox.
When checked, this option disables provisioning of the certificates installed on the current application. This means that Trust Protection Foundation does not attempt to install, renew, process, or validate certificates on the application.
-
(Optional) In the Device Certificate box, click
 to select and associate a certificate with the new application.
to select and associate a certificate with the new application. NOTE If you don't have a certificate ready, you can do this later or you can do it on the certificate's Association tab.
To associate a certificate with the current application, you must have write permissions to the application object and either write or associate permissions to the certificate object.
For detailed information on associating a certificate with an application, see Associating a certificate with an application object.
-
Under General, do the following:
- In the Application Name field, type a name for the new application.
-
(Optional) In the Description field, type a description for the purpose of the application.
A strong description can help to provide context for other administrators who might need to manage the new application.
-
In the Contacts field, select user or group identities you want assigned to this application object (or choose the Use policy value to configure contacts using a policy).
Default system notifications are sent to the contact identities. The default contact is the master administrator.
TIP If the Identity Selector dialog is not populated when it first opens, enter a search query to retrieve the Identity list. The administration console does not automatically display external users and groups. You must first enter a search string so Trust Protection Foundation can query the external Identity store, then return the list of requested users or groups. If you want to display all user or group entries, enter the wildcard character (*).
Press Shift+click to select multiple, contiguous users and groups. Press Ctrl+click to select multiple, discontiguous users and groups.
-
In the Approvers field, select user or group Identities you want to assign to approve workflows (certificate approval or injection command) for the new application.
The default approver is the master administrator. For more information on defining workflow objects, see Implementing certificate workflow management.
-
(Conditional) If your application (or certificate) object is affected by a defined workflow and you want users to use a console other than Policy Tree, click Managed By and select which administration console to use as part of the workflow.
You only need to configure this if you are using workflows and expect users to perform a task using a particular administration console. The default setting is Policy Tree.
For more information, see Specify folders and certificates to be managed by Certificate Manager - Self-Hosted .
-
Under Application Information, do the following:
-
Click
 next to Application Credential to browse for the credential object that you want to use to authenticate with the application.
next to Application Credential to browse for the credential object that you want to use to authenticate with the application.DID YOU KNOW? Credential objects store the credentials Trust Protection Foundation uses to authenticate with devices, applications, and CAs. The stored credential might be a user name or private key credential; some drivers—such as F5, which is not SSH-based—can only use the user name credential for authentication.
NOTE The user account you select must have Read and Write access to the Temporary, Private Key, and Certificate directories.
If you need help with this step, see your system administrator.
For more information, see Working with system credentials.
-
(Optional) In the Port field, type the port that Trust Protection Foundation should use to communicate with the server where the application is installed.
Trust Protection Foundation uses the SSH protocol to communicate with the application server installed on Linux or Windows. The default SSH port assignment is port 22.
-
(Optional) Type the Port used by the DataPower REST Management Interface on which the DataPower endpoint is listening for API connections.
-
-
Complete the settings for the application object by referring to the following table:
Field
Policy
Description
SFTP Configuration
Trust Protection Foundation imports certificates on DataPower devices via SFTP when Connection Method is set to SSH.
Hostname/Address

IP address or hostname of the SFTP server Trust Protection Foundation uses to install certificates on the DataPower device.
Trust Protection Foundation supports both IPv4 or IPv6 connections.
Credential

The user name Credential that Trust Protection Foundation uses to access the SFTP server.
To select a user name credential
- Click
 to open the Credential Selector dialog.
to open the Credential Selector dialog. - In the Credential Selector dialog box, select the Username Credential that Trust Protection Foundation must use to access the CA server, and then click Select.
For more information, see Working with system credentials.
Path

Directory on the SFTP host where Trust Protection Foundation can write (or read) certificate files for import (or export) on the DataPower device.
Port

Port Trust Protection Foundation uses to connect to the SFTP server.
The SFTP default port is 22.
Configuration
The following settings are only relevant if the certificate associated with the current device is managed under the Provisioning level of certificate management.
Provisioning Mode:
Choose either the Advanced (default) or Basic provisioning modes.
Advanced: This is the default setting and is designed to provision the certificate and then bind it to all of the configuration elements on the DataPower device.
To configure Advanced provisioning mode
- From the Provisioning Mode list, select Advanced.
-
In the Application Domain field, specify the domain where the certificate and private key are installed on the DataPower device.
If nothing is specified, the default domain is used.
-
Complete the SSL Profile Configuration settings (described below).
Basic:
Installs the certificate and creates the crypto object that represents the certificate on the DataPower device. With this option, you'll need to perform all of the other DataPower configurations manually.
To configure Basic provisioning mode
- From the Provisioning Mode list, select Basic.
- In the Crypto Certificate field, type the name of your crypto certificate.
- (Optional) In the Crypto Key field, type the name of your crypto key.
-
In the Application Domain field, specify the domain where the certificate and private key are installed on the device.
If nothing is specified, the default domain is used.
To configure the SSL configuration settings via policy, go to the Applications > DataPower tab in the Policy object configuration. The DataPower settings defined in the Policy object may be inherited by all subordinate DataPower application objects.

Associates the specified profile(s) when Trust Protection Foundation provisions a certificate to the DataPower Gateway so that all SSL/TLS services associated with the DataPower Gateway can use the private key and certificate.
Credential Type

Select the type of credential to be created from the provisioned certificate:
- Identification: An identification credential consists of a certificate (which contains a public key) and the corresponding private key. The identification credential is used by the DataPower Gateway when it is an SSL proxy; that is, the SSL Proxy Service sends its certificate to an SSL peer when negotiating an SSL/TLS connection. The certificate may also be used as the identity when signing, encrypting, or decrypting documents.
- Validation: A validation credential is used to authenticate certificates that are received from SSL peers or to validate certificates that are used in digital signature and encryption operations. An SSL client requires a validation credential object only when it authenticates the certificate presented by the remote SSL server. An SSL server requires a validation credential object only when it authenticates remote SSL clients. The SSL standard does not require authentication of the server or client certificates.
Profile Type

Select the type of profile to which the certificate is bound:
-
SSL Proxy: An SSL proxy profile is a legacy object that, in conjunction with a crypto profile, is used to secure inbound and/or outbound connections with the DataPower Gateway.
TIP SSL Proxy Profiles were deprecated in firmware version 7.2 but are still supported.
- SSL Client: An SSL client profile is used to secure outbound connections between the DataPower Gateway (acting as a client) and servers.
- SSL Server: An SSL server profile is used to secure inbound connections between clients and the DataPower Gateway (acting as a server).
For more information, visit https://www.ibm.com/support/knowledgecenter/en/SS9H2Y_7.5.0/com.ibm.dp.doc/sslconnections.html
Crypto Profile Name
Specify the name of your Crypto Profile with which to associate the SSL Proxy Profile.
SSL Proxy Profile Name

Specify the name of the SSL Proxy Profile (deprecated) with which to bind the provisioned certificate. If the profile does not exist, it will be created.
SSL Client Profile Name

Specify the name of the SSL Client Profile with which to bind the provisioned certificate. If the profile does not exist, it will be created.
SSL Server Profile Name

Specify the name of the SSL Server Profile with which to bind the provisioned certificate. If the profile does not exist, it will be created.
Certificate and Private Key Settings
Certificate Folder

Specify the target folder for the certificate being provisioned.
The cert: option is the default certificate folder.
When you select the sharedcert: option, the certificate is provisioned into the default domain and the Application Domain setting applies to all other objects (Crypto Certificate, Crypto Key, Crypto Profile, etc.).
For more information about the DataPower requirements related to this setting, visit:

Installs the root and intermediate root certificates required to support the signature chain with the current certificate.
Password Alias

This IBM DataPower password map establishes a mapping between an alias and its corresponding plaintext password. The alias is a publicly known reference included in configuration files and reports. Leveraging this alias ensures the confidentiality of the actual password, as its plaintext form is securely stored in an encrypted file. Consequently, the password linked to the alias remains inaccessible and undisclosed to unauthorized individuals.
NOTE This feature will not keep in sync with passwords under Password Alias. Using a different "Private Key Password Credential" in Trust Protection Foundation doesn't update the existing Password Alias on DataPower.
This enhancement utilizes existing aliases in DataPower. A new Password Alias will be created if no alias exists and a "Private Key Password Credential" is provided in Trust Protection Foundation.
Private Key Password Credential

The credential that defines the password used to encrypt the private key before it is provisioned to the file on the DataPower Gateway.
NOTE This credential is not applicable when provisioning a validation credential in Advanced mode, or when provisioning only a crypto certificate in Basic mode.
To select a private key password credential
-
Click
 to open the Credential Selector dialog.
to open the Credential Selector dialog. -
Select the credential required to access the private key file for certificate renewal, and then click Select.
For more information, see Working with system credentials.
Use FIPS

NOTE The Federal Information Processing Standard (FIPS) option for private key storage is not supported for DataPower in this release of Trust Protection Foundation. Please contact CyberArk Support with any questions or concerns.
Certificate File
The filename Trust Protection Foundation generates automatically for the certificate when it installs the certificate.
This is not an editable field.
Certificate Alias
Alias that is assigned to DataPower objects related to the certificate (i.e. Crypto Certificate, Identification Credential, and Validation Credential).
When using Advanced provisioning mode, this is not an editable field.
Private Key File
The filename Trust Protection Foundation generates automatically for the private key file when it installs the private key.
This is not an editable field.
Private Key Alias
Alias that is assigned to DataPower objects related to the private key (i.e. Crypto Key).
When using Advanced provisioning mode, this is not an editable field.
(Conditional) Private Key Password/Confirm
The password required to access the private key.
This option is available only when you click Edit to enter the Certificate and Private Key settings for a certificate and private key not installed by Trust Protection Foundation.
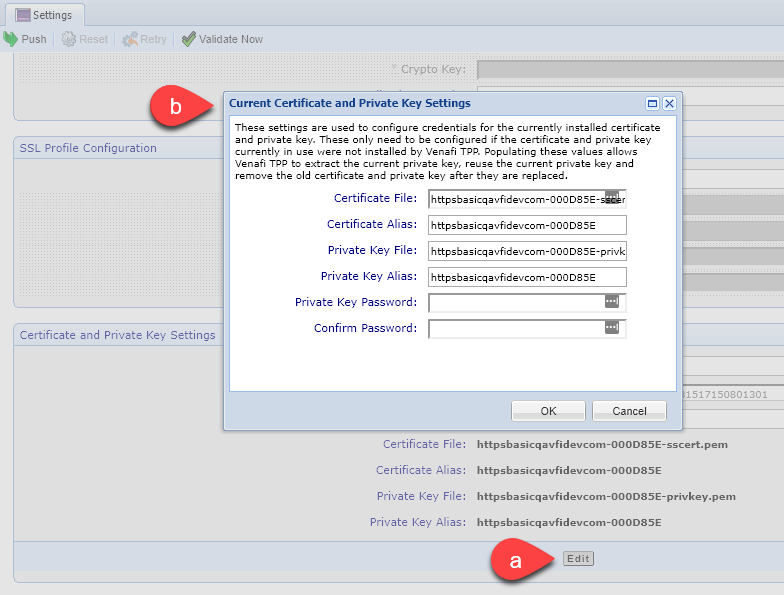
- Click Edit to open the Current Certificate and Private Key Settings box.
- Type the settings for the currently installed certificate and private key, and then click OK.
These values need to be configured only if the current certificate and private key were not installed by Trust Protection Foundation.
Trust Protection Foundation uses the values to create Generational Credential objects for the currently installed certificate and private key. Populating these values allows Trust Protection Foundation to extract the current private key, reuse the current private key, and remove the old certificate and private key after they are replaced.
For more information on Generational credentials, see Working with system credentials in the CyberArk Trust Protection Foundation Administration Guide.
- Click
-
When you are finished, click Save.
-
On the application's Settings sub-tab:
-
Click
 to push a certificate to its associated application.
to push a certificate to its associated application.For more information, see Pushing a certificate and private key to an application .
- Click
 Reset to stop processing the application and reset the status and stage.
Reset to stop processing the application and reset the status and stage. - Click
 to reattempt installation of the certificate to its associated application, .
to reattempt installation of the certificate to its associated application, . -
Click
 Validate Now to validate the applications associated certificate.
Validate Now to validate the applications associated certificate. Validation requests are placed into a queue. When your validation runs, the application and its associated certificate are scanned according to the settings configured in the application object’s Validation tab.
For more information, see About certificate and application validation.
-
-
On the application object's Validation tab, you can configure validation settings for the application object.
-
On an object's General tab:
-
Click the Log sub-tab to view any events that are triggered by the template object.
-
Click the Permissions sub-tab to configure the users or groups to whom you want to grant permissions to the new object. For more information, see Permissions overview.
-
What's next?
After you've created an application object, here are other things you can do to manage the new application: