Integrating Google Cloud Load Balancer with CyberArk
The CyberArk Trust Protection Foundation™ Google Cloud Load Balancer driver supports global and regional (HTTPS) proxies, which are used by external and internal HTTPS load balancers.
This topic provides the information you need to manage certificates on your external load balancers.
For information about version dependencies, see Certificate installation (provisioning) driver support.
DID YOU KNOW? Keep in mind that certificates you plan to provision must have the encryption algorithm set to either RSA-2048 or ECDSA P-256. Click here for more details for more details found in the Google Cloud Load Balancer documentation.
First things first
Before you start configuring integrations with Google Cloud Load Balancer, carefully review this high-level diagram. It can really help you complete your integration faster.
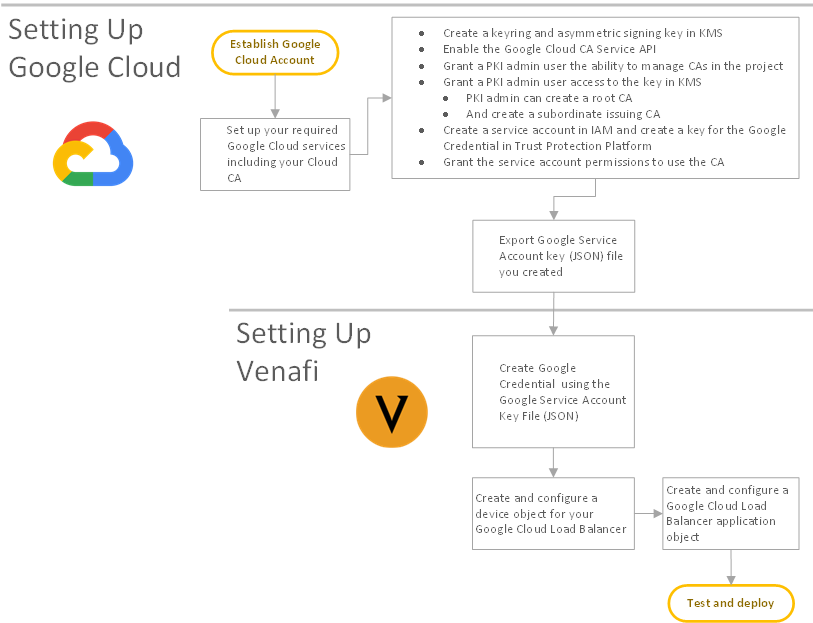
TIP For a rather nifty and helpful overview of the steps for integrating applications with CyberArk, look here.
To complete your integration, complete the following steps:
Google knows its stuff best, so we won't presume to give you all the details when using Google products. We strongly suggest that you carefully review and follow Google documentation to establish your Google Cloud account.
IMPORTANT Here are the minimum permissions you must set up on the Google Cloud side:
- compute.sslCertificates.create
- compute.sslCertificates.delete
- compute.sslCertificates.get
- compute.targetHttpsProxies.get
- compute.targetHttpsProxies.setSslCertificates
- compute.targetSslProxies.get
- compute.targetSslProxies.setSslCertificates
-
compute.regionSslCertificates.create
-
compute.regionSslCertificates.delete
-
compute.regionSslCertificates.get
-
compute.regionTargetHttpsProxies.get
-
compute.regionTargetHttpsProxies.setSslCertificates
-
compute.regions.list
Not required but additional permissions used by Google Cloud Load Balancer application driver:
-
compute.targetHttpsProxies.create
-
compute.regionTargetHttpsProxies.create
-
compute.regionUrlMaps.use
-
compute.urlMaps.use
When you've done the Google thing, then you're ready to configure the CyberArk side.
Make sure you've already set up your Google Cloud account and configured your Load Balancer. Your Google account must be up and running for CyberArk to connect and do its thing.
First things first
Let's take care of prerequisite steps first.
- Make sure you have the right permissions to the Policy folder in WebAdmin where you'll be doing the configuration. Specifically, you'll need
- View/Read/Write permissions for uploading your Google Service Account Key File
To create the Google Cloud Load Balancer application object, you need View, Read, Write, and Create permissions on the corresponding policy (folder) where you create the object.
- Read and Write access to the Temp Directory defined in the Device object.
- Make sure you have your Google Service Account Key File ready for uploading to CyberArk. You'll need it!
TIP Not sure how to set permissions on Policy folders? Look here, and then come back when you're ready.
Creating a Google Credential
A Google credential object is used by CyberArk Trust Protection Foundation to store your Google Cloud Service Account Key file. Your Google Service Account is used by CyberArk Trust Protection Foundation to access your Google Cloud CA and Google Cloud Load Balancer.
TIP If you're a developer, you might be interested in knowing that the Google credential is defined in the schema using the Google Credential class and implemented in Venafi.Drivers.GoogleCredential: CredentialObject.
To create a new Google Credential
-
From the Certificate Manager - Self-Hosted menu bar, click Policy Tree.
- From the Policy tree, select the folder where you want to create the Google Credential, and then click Add > Credential > Google Credential.
- In Credential Name, type a name for the new credential.
- Click Upload Google Service Account Key File (button near the top of the page), locate the JSON file, and then click Upload.
- Click Save.
Creating a device object for Google Cloud Load Balancer
There's actually nothing special or unusual about creating a device object for Google Cloud Load Balancer. But it's good to note that for this driver, device details (host/login credentials) are irrelevant. That's because the Google Credential takes care of that for you. So no need to fill in those details when you create the device object.
If you've never created a device object on the CyberArk Platform, these steps can help you through it.
Either way, come back here when you're finished and we'll take the next (and final) step.
Creating a Google Cloud Load Balancer application object
Trust Protection Foundation uses the information you'll supply in a Google Cloud Load Balancer application object to manage certificates installed on Google Cloud Load Balancer devices.
To create and configure a Google Cloud Load Balancer application object
-
From the Certificate Manager - Self-Hosted menu bar, click Policy tree.
- In the Policy tree, select the device object to which you want to add the new application object, and then click Add > Application, and then select Google Cloud Load Balancer.
-
When the new application object page appears, then under Status, clear the Processing Disabled checkbox.
When checked, this option disables provisioning of the certificates installed on the current application. This means that Trust Protection Foundation does not attempt to install, renew, process, or validate certificates on the application.
-
(Optional) In the Device Certificate box, click
 to select and associate a certificate with the new application.
to select and associate a certificate with the new application. NOTE If you don't have a certificate ready, you can do this later or you can do it on the certificate's Association tab.
To associate a certificate with the current application, you must have write permissions to the application object and either write or associate permissions to the certificate object.
For detailed information on associating a certificate with an application, see Associating a certificate with an application object.
-
Under General, do the following:
- In the Application Name field, type a name for the new application.
-
(Optional) In the Description field, type a description for the purpose of the application.
A strong description can help to provide context for other administrators who might need to manage the new application.
-
In the Contacts field, select user or group identities you want assigned to this application object (or choose the Use policy value to configure contacts using a policy).
Default system notifications are sent to the contact identities. The default contact is the master administrator.
TIP If the Identity Selector dialog is not populated when it first opens, enter a search query to retrieve the Identity list. The administration console does not automatically display external users and groups. You must first enter a search string so Trust Protection Foundation can query the external Identity store, then return the list of requested users or groups. If you want to display all user or group entries, enter the wildcard character (*).
Press Shift+click to select multiple, contiguous users and groups. Press Ctrl+click to select multiple, discontiguous users and groups.
-
In the Approvers field, select user or group Identities you want to assign to approve workflows (certificate approval or injection command) for the new application.
The default approver is the master administrator. For more information on defining workflow objects, see Implementing certificate workflow management.
-
(Conditional) If your application (or certificate) object is affected by a defined workflow and you want users to use a console other than Policy Tree, click Managed By and select which administration console to use as part of the workflow.
You only need to configure this if you are using workflows and expect users to perform a task using a particular administration console. The default setting is Policy Tree.
For more information, see Specify folders and certificates to be managed by Certificate Manager - Self-Hosted .
- Under Application Information, click
 to select your Google Credential that you created earlier.
to select your Google Credential that you created earlier. - The Project ID is populated using the project from the valid Google Credential. This provides a way to specify in which project the Private CA is placed. The value of the field is extracted from the Google Credential, which the user has the option to edit.
-
Under Installation Settings, specify target proxy server information.
If you specify Internal HTTPS, as the Target Proxy Type, make sure to specify its correct region in the Target Region field.
You can provision to an existing proxy; or a new one can be created if a correct and existing Target Resource is specified.
For HTTPS proxies, type the existing URL Map in Target Resource; and for SSL proxies, enter an existing Backend Service.
The provisioned certificate will not bind to a Google resource if the Target Proxy Name is left empty. Otherwise, we will bind the certificate to the Target Proxy Name.
DID YOU KNOW? If you try to provision to a Google Cloud Load Balancer and you either 1) left the Target Resource field blank, or 2) had specified a target resource that does not exist, then Trust Protection Foundation attempts to retrieve the target resource from the cloud service automatically and populates the Target Resource field with the relevant one. Either way, a warning is logged for the Google Cloud Load Balancer application object.
-
When you're finished, click Save.